Most companies, especially small and medium businesses, do not fight against targeted attacks. Instead, they are dealing with generic attacks, botnets, mass exploitation and cybernoise. Why? Because it’s effective. Learn more about cybernoise and how its massive volume complicates effective cyberdefense.
For Czech and Slovak readers: Přečtěte si tento článek v češtině v časopise IT Systems zde.
What is cybernoise
Cybernoise is constantly generated as a result of various automated processes, routine activities, and other operations monitoring the Internet. Whether it’s legitimate business, academic research, or criminal activity, this probing contributes to continuous data traffic, making it difficult to distinguish the important from the noise, targeted attacks from random generic attacks, and good intentions from malicious ones
In addition to the traffic generated by botnets and untargeted mass exploitation attempts, there is also cybernoise created by e.g. search engines targeting devices connected to the Internet (such as Shodan.io or Censys.io). This background noise also consists of automated traffic from various webcrawlers, bots, or brute force attacks. Dealing with this unwanted traffic is a challenging task for organizations.
The average company detects access from tens of thousands of unique IP addresses every day. Each of these IPs can generate hundreds to thousands of events that may require the attention and analysis of the security team. So, while security analysts investigate alerts caused by botnets or amateur hackers, a real attacker may avoid early detection and penetrate a corporate network unnoticed.
Small and medium-sized companies are not in a war against targeted attacks. They are fighting generic attacks, bots, mass exploitation, and random cybernoise.
Most companies, especially small and medium-sized businesses, are not in a war against targeted attacks. They are fighting generic attacks, botnets, mass exploitation, and random cybernoise. Why? Because it works. The reason we see millions of attacks every day is because of their effectiveness. It’s almost free. Hitting tens of thousands of small and medium-sized businesses with botnet agents or ransomware may not get attackers into a “golden Lamborghini,” but it will likely help them achieve their goals without attracting increased attention from law enforcement or security agencies (at least for a while).
Before you dismiss this problem as irrelevant, ask yourself: Do you already have SIEM, SOAR, XDR implemented? Do you have a team of experienced analysts monitoring your organization 24/7? Are you using your existing security tools and platforms in full capacity with all available options? Unfortunately, for most SMBs, the answer will be “no,” which is why they fall easy prey.
How can we reduce the impact of increasing cybernoise?
- Implement at least basic cybersecurity measures: Even basic measures can do a great deal of work. Use a firewall, update your software regularly, and ensure your systems are protected against known vulnerabilities.
- Utilize what you have: Your organization most likely already has a next-gen firewall. Set up useful features like dynamic firewall lists and intrusion prevention/detection systems (IDS/IPS). Maximize the usefulness of your firewall through proper configuration and use.
- Integrade new next-gen highly accurate threat lists on your existing firewalls: Integrate ELLIO: Threat List MAX on your existing next-gen firewalls. You efficiently and automatically filter out unwanted traffic at the perimeter level. Also, ELLIO: Threat List mitigates the risk of DDoS attacks and new attacks for which detections are yet not available.
- Use anti-malware solutions: Regular scanning and real-time protection features help reduce risks.
- Back up your data regularly: In case of a ransomware attack, up-to-date backups are crucial. Make sure your backups are stored securely and test them regularly.
- Monitor network traffic: While SMBs may not have sophisticated monitoring systems like SIEM or SOAR, simple network monitoring tools can help identify unusual activities that may indicate an attack.
- Develop a response plan: Know what to do in case of a cyber incident. A response plan helps mitigate damage and recover faster from an attack.
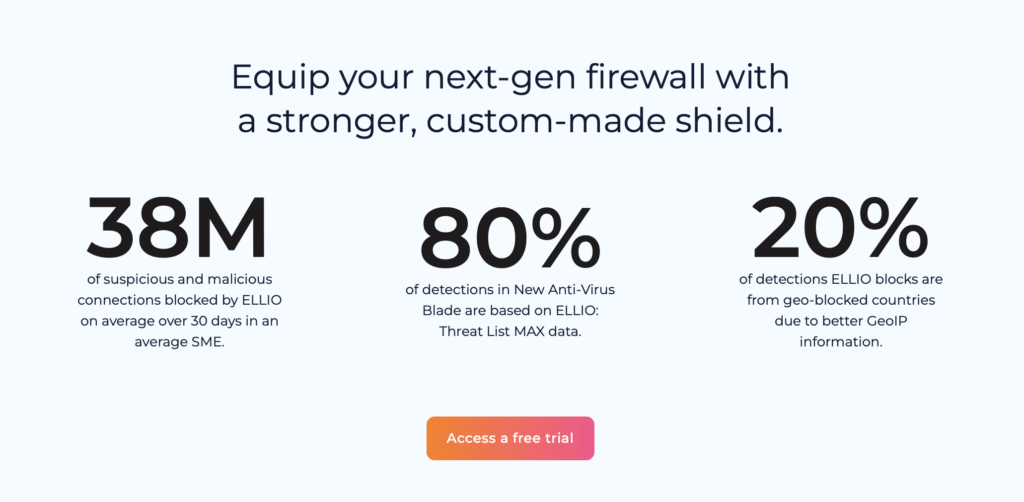
ELLIO boosts firewall protection quickly, reliably, and efficiently.
If you’re looking for an easy and effective way to boost your firewall protection, ELLIO is the solution. It provides real-time IP blocking to help keep malicious IPs away from your network. With ELLIO, you’ll get reliable security along with the IP Lookup and Blocklist Management Platform for added peace of mind.
Try a free trial at https://ftl.ellio.tech/auth/registration
About ELLIO
ELLIO is a leading expert on mass exploitation, cyber deception, and opportunistic reconnaissance, delivering real-time, accurate threat intelligence to automate triage and reduce alert fatigue in SIEM, SOAR, TIP, accelerate incident response and threat hunting. ELLIO also offers the largest and most dynamic threat lists (blocklists) and blocklist management platform to strengthen perimeter and firewall defences. https://ellio.tech
Useful links
- Explore ELLIO: Threat List MAX, the largest and most dynamic IP blocklist on the market, compatible with all popular next-gen firewalls.
- Use a free ELLIO IP Lookup to check suspicious IPs.
- Try ELLIO: Blocklist Management with a 7day trial.
- Download ELLIO Free Community IP Blocklist.
- Check out ELLIO: Threat Intelligence to reduce alert fatigue and speed up threat hunting.


