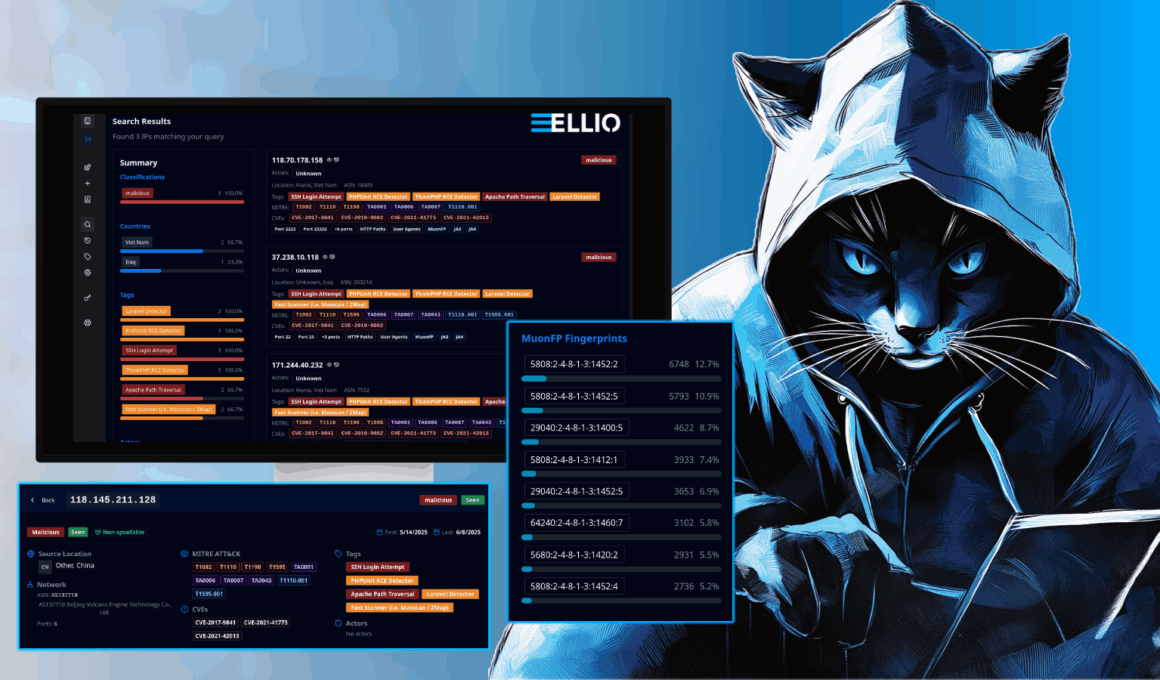
This June, ELLIO team introduces new features of ELLIO Threat Platform to help Threat Hunters and Incident Response teams dive deeper into threats and accelerate their investigations. These improvements transform how to analyze and correlate threat data in the platform.
What’s new?
- New SSH credential intelligence for spotting brute force campaigns.
- MITRE ATT&CK® integration for better threat mapping.
- Tuned fingerprint analysis to catch coordinated activity.
ELLIO Threat Platform gives real-time visibility into reconnaissance and mass exploitation activity. Built on a global deception network, it highlights high-confidence signals like brute force attempts, exploit scans, and coordinated probing, while filtering out background grey noise.
With automated blocklists, advanced fingerprinting, and MITRE ATT&CK® mapping, it supports incident response and threat hunting teams by helping detect early-stage threats, uncover behavior patterns and anomalies, enrich alerts, and block malicious traffic before it escalates.
Update #1: SSH Credential Intelligence: Exposing brute force campaigns
Understanding SSH attack patterns is essential for defending against unauthorized access. The new SSH Credentials feature provides clear visibility into authentication attempts targeting infrastructure. It enables quickly detect credential reuse across multiple sources, coordinated brute force campaigns, high-value accounts under attack, and the evolution of attack techniques over time.
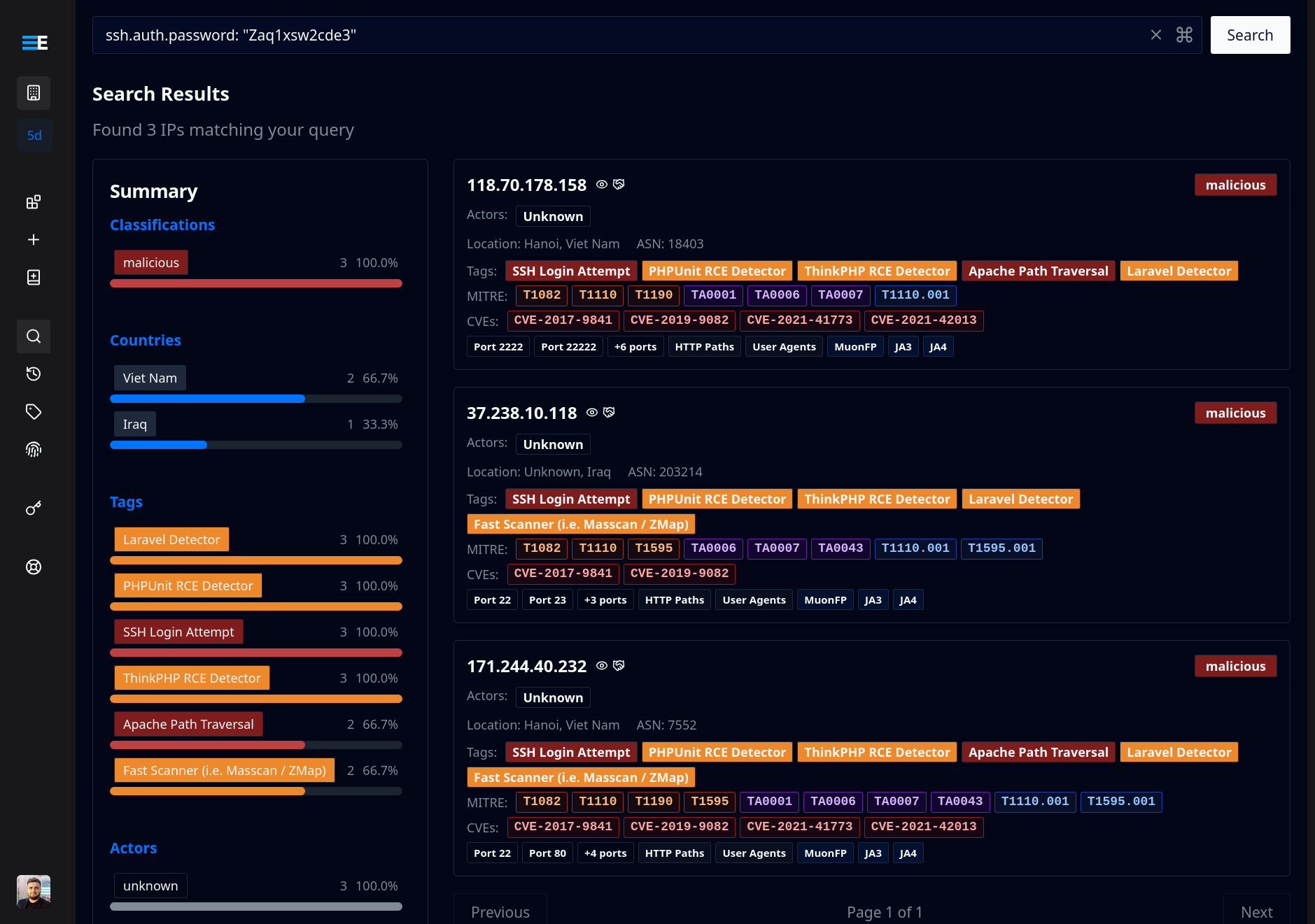
What’s new:
- Credential Tracking: View all SSH username and password combinations attempted by any IP address over the last 90 days.
- Advanced Pattern Matching: Use wildcards and fuzzy matching to find specific password patterns.
- Interactive Search: Click any credential to find other targets using the same username or password.
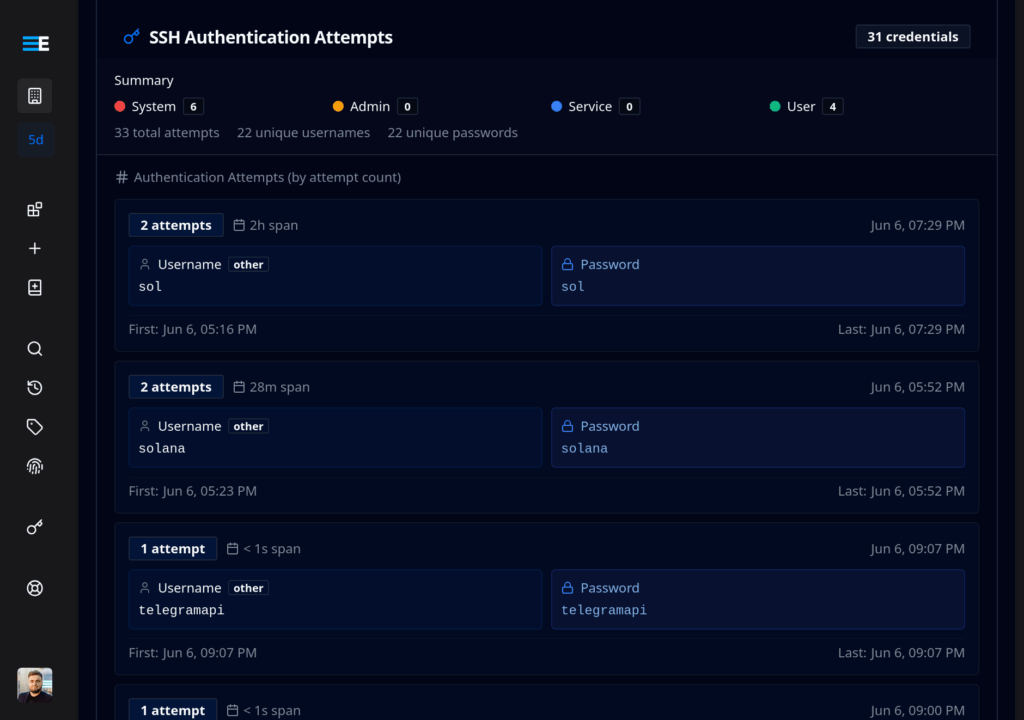
Security teams now quickly identify:
- Credential reuse patterns by multiple sources
- Coordinated brute force campaigns
- High-value administrative accounts under attack
- Evolution of attack techniques over time
Search examples:
ssh.auth.username: "admin"
ssh.auth.password: "*123*"
ssh.auth.password: "????????????*"
ssh.auth.username: "root" AND ssh.auth.password: "root"Update #2: MITRE ATT&CK® integration for better threat mapping
This update fully integrates MITRE techniques, tactics, and sub-techniques into the ELLIO Threat Platform, making it easier and faster to connect observed threats with established frameworks. This enables analysts to quickly map threats to known frameworks, identify emerging adversary methods, correlate related attacks, and build detailed threat profiles aligned with industry standards.
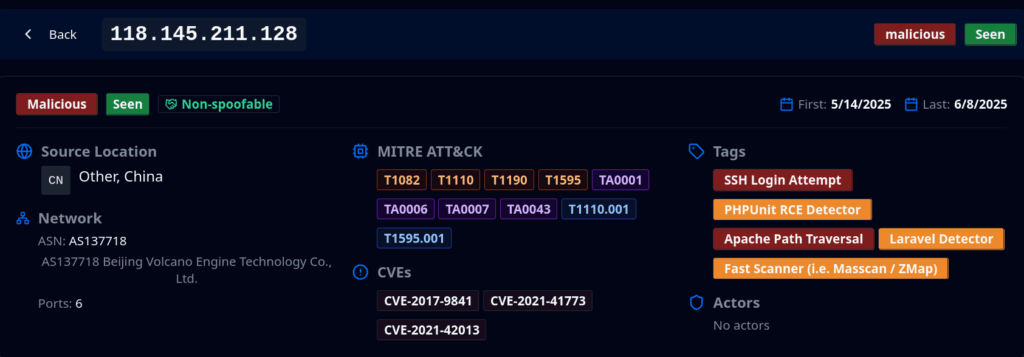
What’s new:
- Native MITRE Search: Search directly by technique IDs (T1595), tactic IDs (TA0043), or sub-technique IDs (T1595.001).
- Aggregated Analytics: See top MITRE elements across search results to identify trending TTPs.
- Visual Classification: Color-coded badges distinguish techniques (orange), tactics (purple), and sub-techniques (blue).
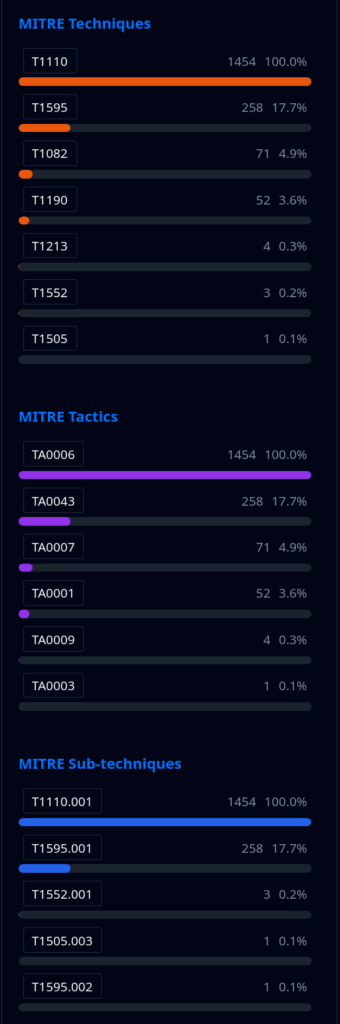
MITRE ATT&CK integration enables analysts to quickly:
- Map observed threats to known attack frameworks
- Identify emerging tactics and techniques
- Correlate threats based on adversary behavior
- Build detailed threat profiles aligned with industry standards
Search examples:
mitre_attack.techniques: "T1190"
mitre_attack.tactics: "TA0001" AND src.geo.country.code: "CN"
mitre_attack.sub_techniques: "T1552.001"Update #3: Enhanced Fingerprint Intelligence to spot patterns faster
Fingerprint-based analysis are extremely useful for spotting patterns that traditional indicators often miss. They help identify coordinated activity, tie together seemingly unrelated threats, and cut through noisy traffic. With this update, working with fingerprints in ELLIO Threat Platform is faster, clearer, and more actionable than ever.
These upgrades make it easier to track coordinated campaigns, pivot between signals, and focus on what matters most: high-frequency, high-impact threat patterns.
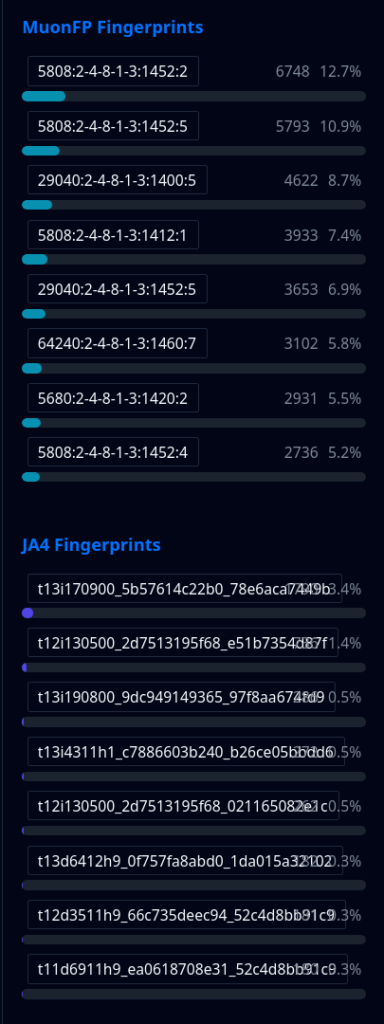
What’s new:
New Search Results Aggregation: View top fingerprints across your search results to identify common patterns.
New Pattern Recognition: Quickly spot frequently occurring TCP (MuonFP) and TLS (JA3/JA4) fingerprints.
New One-Click Analysis: Click any fingerprint in the results sidebar to narrow-down the search for all IPs using that signature.
Search examples:
fingerprints.ja4: "t13i170900_5b57614c22b0_78e6aca7449b"
fingerprints.muonfp: "1024:*:*:*" AND spoofable: "false"Get a closer look at ELLIO with a free trial
Give the ELLIO Threat Platform a spin and see how it helps you spot threats faster, dig deeper into investigations, and block malicious traffic early without manual unnecessary efforts. No pressure. Just real, actionable intel from day one.
Got thoughts on the new features? We’d love to hear them.
These updates came directly from user feedback, and your input helps shape what we build next.
ELLIO is a commercial research lab specializing in real-time detection and in-depth analysis of mass exploitation and recon activity. We uncover attack patterns, anomalies, and emerging threats – delivering actionable threat intelligence and tailored solutions to optimize existing resources, mitigate risks, and prevent losses from mass exploitation and network recon.