In November 2024, ELLIO expanded its Deception Network with new honeypots and sensors to tackle the growing wave of mass exploitation and scanning activity. These upgrades improve real-time detection and deep-dive analysis of exploitation attempts and opportunistic reconnaissance.
Mass exploitation has rapidly become a dominant infection vector, surpassing botnets in driving ransomware incidents. Recent research highlights the explosive growth in both the volume and severity of attacks, with high-profile vulnerabilities like MOVEit, CitrixBleed, Cisco XE, FortiOS, Ivanti ConnectSecure, PAN-OS, Junos, and ScreenConnect being widely exploited.
From analysts to executives, cybernoise disrupts everyone.
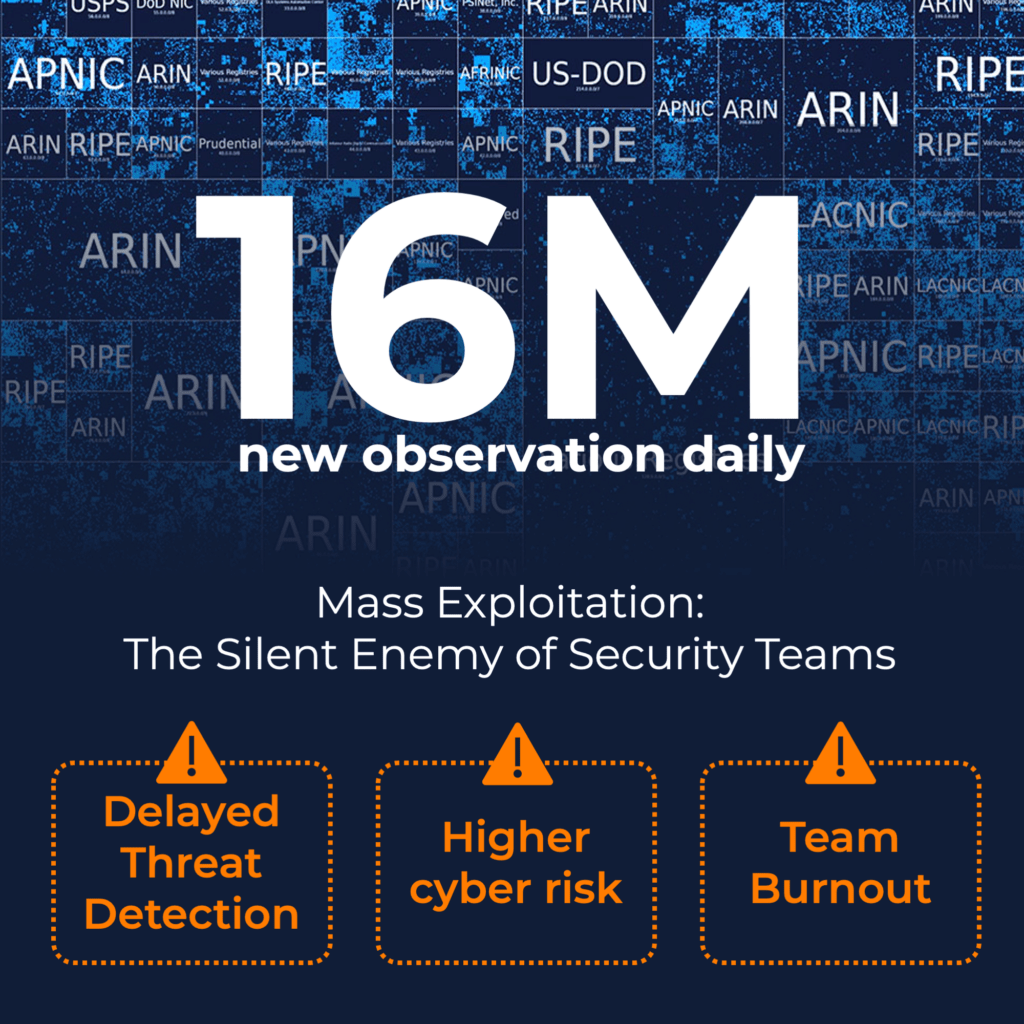
The ELLIO Deception Network detects 16M new observations daily, with the volume continuing to rise. On average, analysts spend over a third of their time chasing down incidents that either aren’t real or were flagged as critical by mistake. Even with advanced tools and skilled experts in place, the risk of missing real cyber threats remains high.
The growing wave of mass exploitation, automated bots, and large-scale scanning attacks is becoming a serious “silent” threat for security teams. These attacks, constantly on the lookout for vulnerabilities, are overwhelming systems and making it harder to spot real threats and targeted attacks in time.
“This cybernoise isn’t just frustrating for analysts. It’s also a challenge for business leaders. Rising cybersecurity costs don’t always deliver the results they should because all this noise lowers productivity and slows down both systems and teams,” adds Jana Tom, COO at ELLIO
16M unique observations daily.
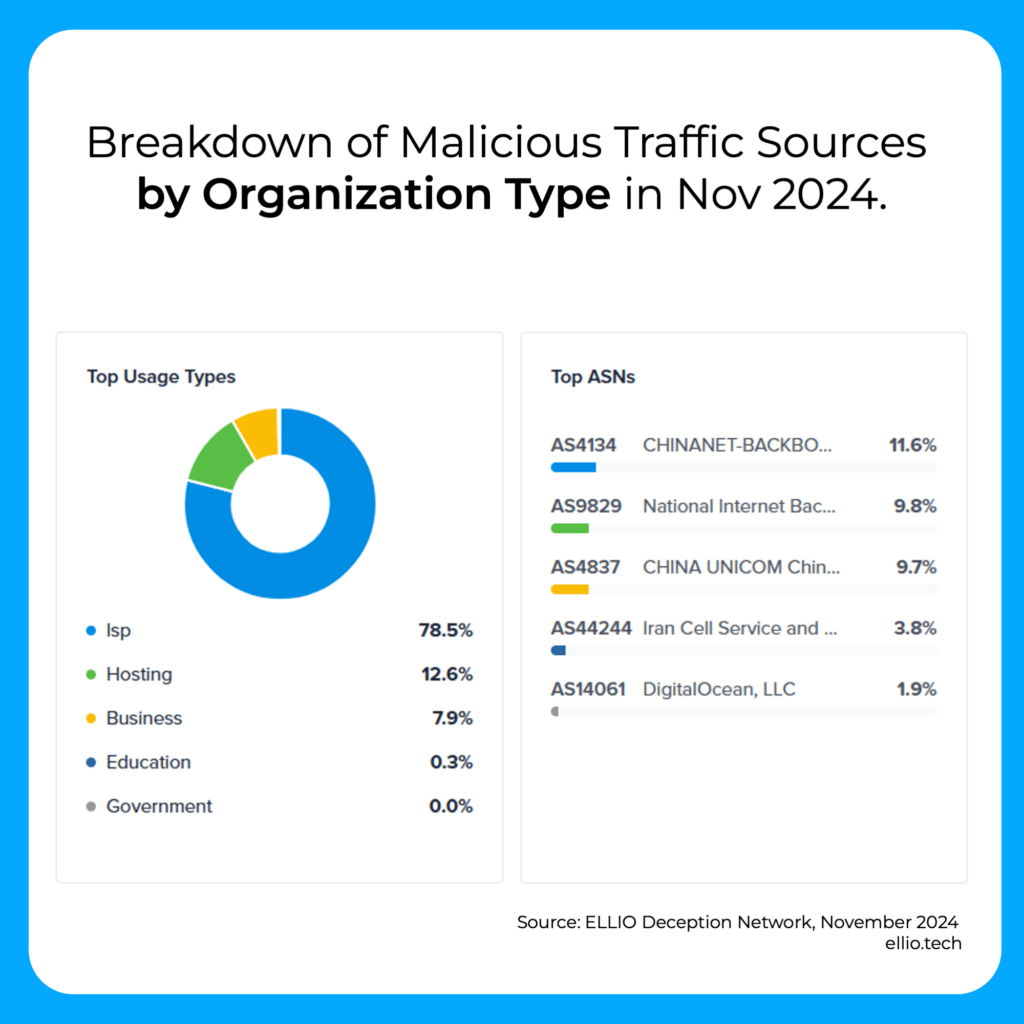
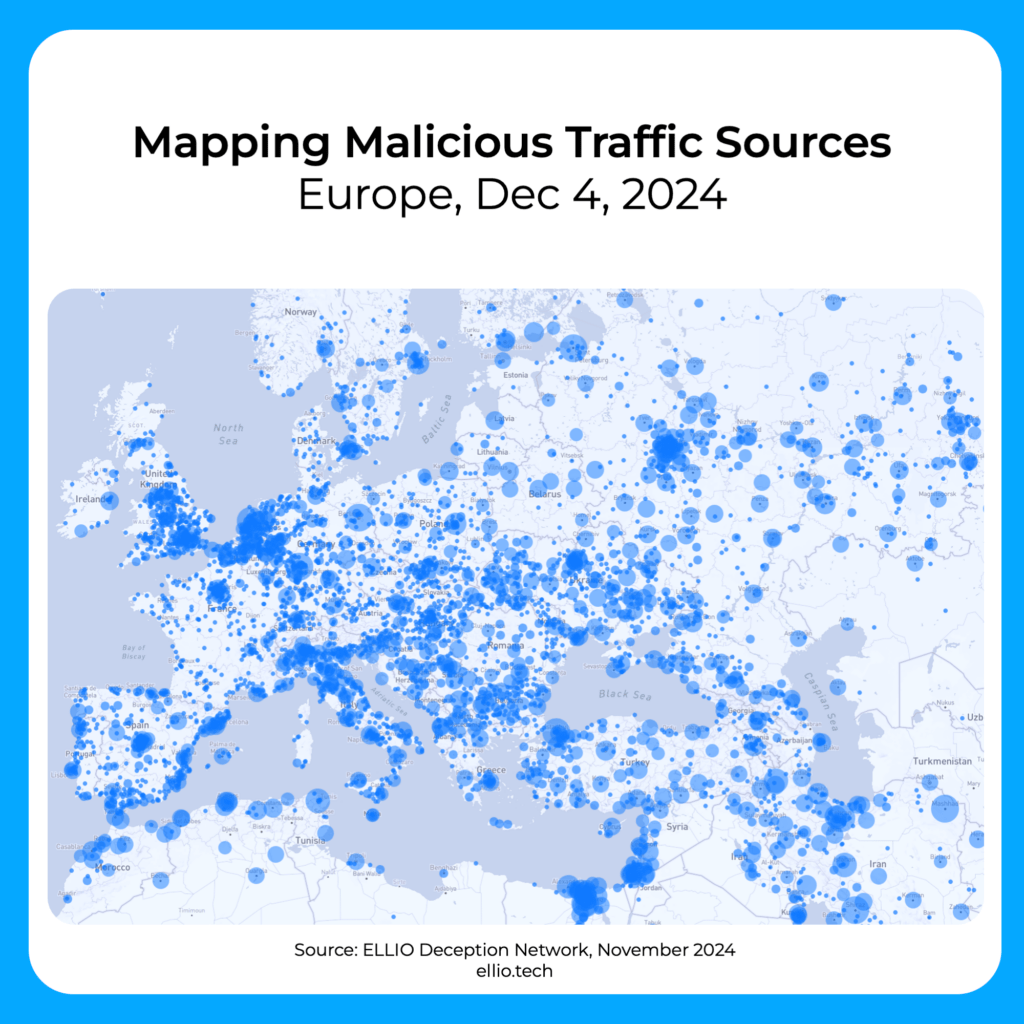
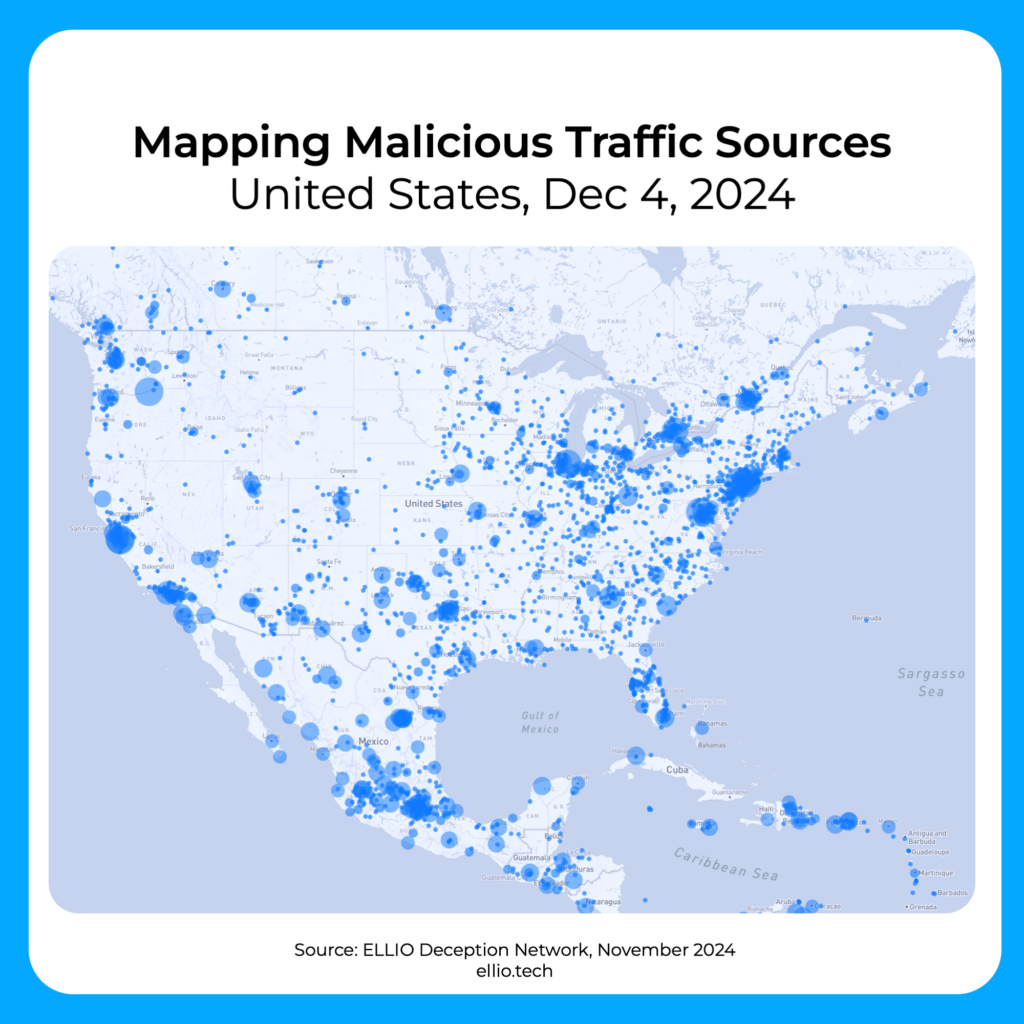
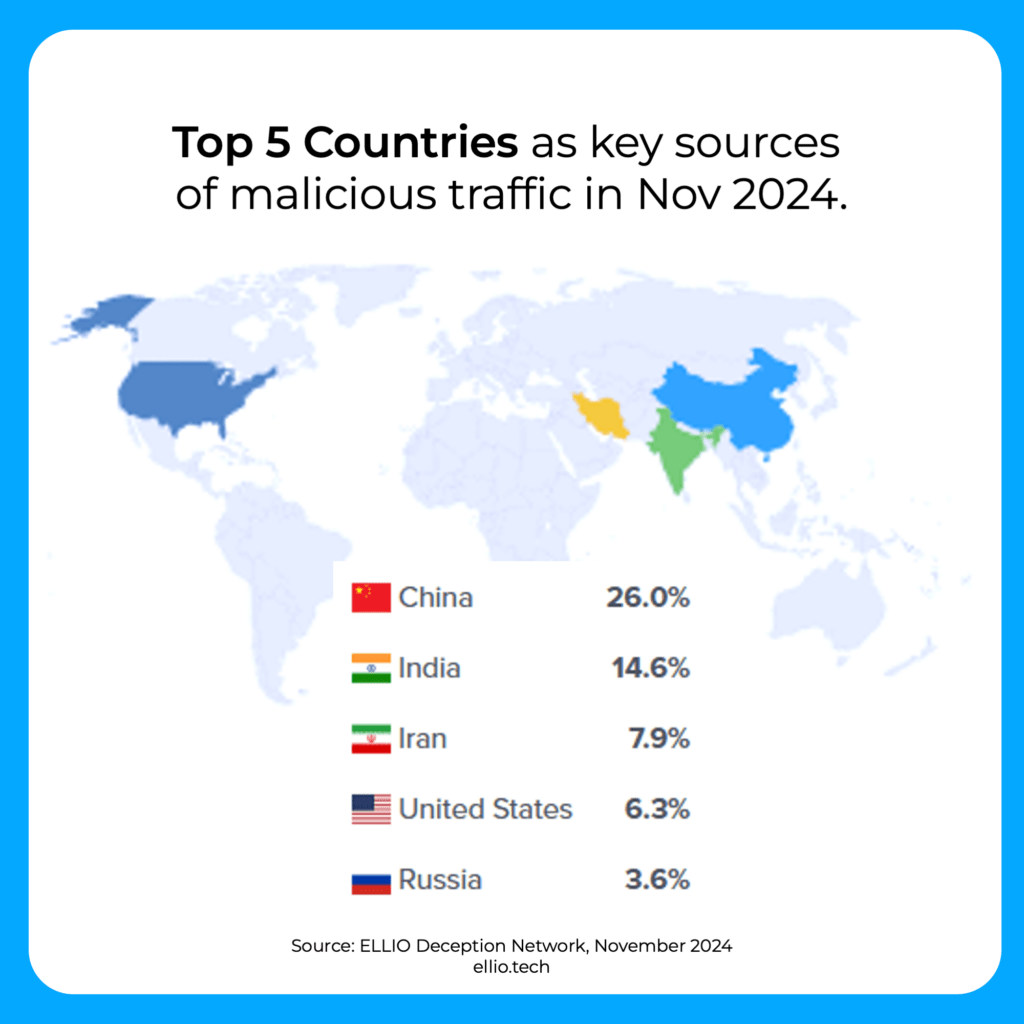
Take a look at the latest stats on mass exploitation from the ELLIO Deception Network in November 2024.

Topics you might find interesting
- Automated tagging and filtering non-critical events in your SIEM, SOAR, TIP in real-time.
- Get a Virtual SOC Analyst to reduce alert fatigue.
- Mass attack data enrichment for faster threat hunting and vulnerability management.
- Network masking from Scanning Services, which are used by attackers to easily locate new targets.
- Learn more about ELLIO, experts on mass exloitation, opportunistic recon, and cyber deception.
Useful links
- Check out ELLIO: Threat Intelligence to reduce alert fatigue and speed up threat hunting.
- Try ELLIO: Blocklist Management with a 7day trial.
- Use a free ELLIO IP Lookup to check suspicious IPs.
- Explore ELLIO: Threat List MAX, the largest and most dynamic IP blocklist on the market, compatible with all popular next-gen firewalls.
- Download ELLIO Free Community IP Blocklist.
More about ELLIO at https://ellio.tech.


