Cybersecurity took center stage in late April and early May 2025, as San Francisco transformed into the beating heart of the global security community. From RSAC and BSides San Francisco to HackTheBay and the AMTSO Networking Reception, the city buzzed with conversations about the future of digital defense.
Amid this high-energy backdrop, ELLIO hit the road to spotlight a fast-evolving threat: mass scanning and reconnaissance. At each stop, from San Francisco to our final session at BSides Nashville, we shared how attackers use scanning at scale and how defenders can fight back.
5 Takeaways from ELLIO U.S. Spring Roadshow:
- Mass scanning is no longer just background greynoise: What used to be considered harmless internet “chatter” has evolved into a structured, weaponized phase of modern cyberattacks. Mass scanning is now often the first step in identifying weak points across vast IP ranges, laying the groundwork for targeted exploitation.
- Reconnaissance leaves a trail (if you know where to look): Sophisticated attackers use proxies, VPNs, and jump servers to hide their tracks, but they still leave behavioral signatures. By analyzing TLS handshakes, HTTP headers, and connection patterns, defenders can trace infrastructure reuse and link seemingly unrelated attacks.
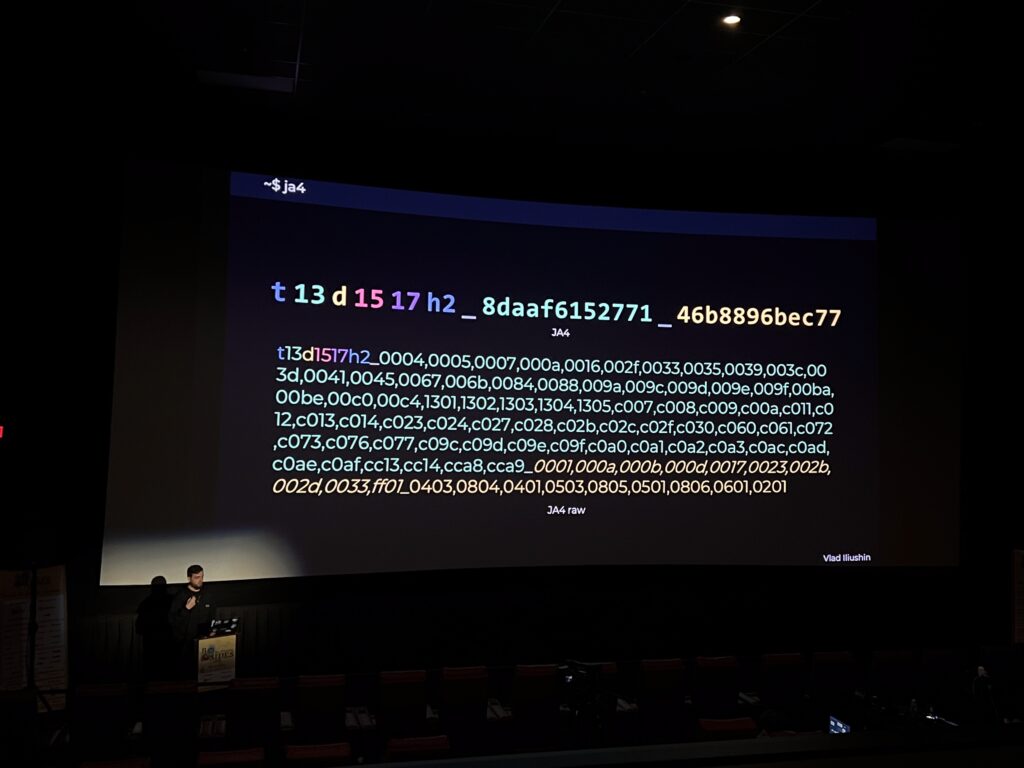
- Network fingerprinting reveals more than you think: Advanced network fingerprinting techniques like JA4, JA4+, and MuonFP can unmask the tooling, tactics, and infrastructure behind an attacker’s scans. From identifying specific malware families to distinguishing between human and automated behavior, fingerprints tell a deeper story.
- Defensive fingerprinting has its limits: While fingerprinting is powerful, it’s not a silver bullet. Spoofed headers, encrypted traffic, and evolving attacker tactics can degrade its reliability. Successful use depends on contextual analysis and correlation with other threat intelligence sources.
- At RSAC 2025: AI and identity take center stage: The major theme at RSAC 2025 was the intersection of AI and identity protection. From generative AI-powered phishing to deepfake-driven social engineering, identity has become the new perimeter – and it’s under constant siege.
Mapping the invisible: The power of network fingerprinting.
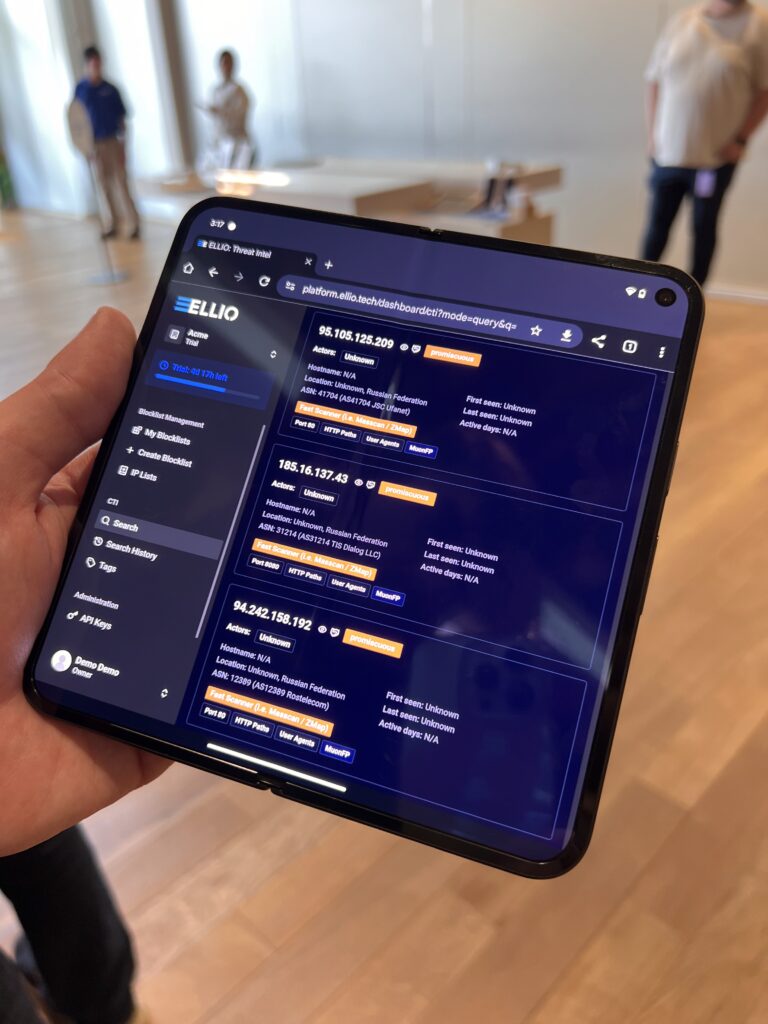
As scanning and reconnaissance tactics grow more diverse – from public platforms like Shodan and Censys to stealthy probing by botnets and bulletproof hosting services – security teams need sharper tools to understand who’s knocking on their digital doors. The ELLIO team shared its latest research on the evolving mass scanning landscape and its growing threat at key cybersecurity events, including BSides San Francisco, HackTheBay 2.0, and BSides Nashville. For those looking to dive deeper, we also hosted the ELLIO Recon Breakfast and an in-depth ELLIO Recon Workshop in San Francisco during RSAC 2025.

Vlad Iliushin, CEO of ELLIO, a research lab specializing in the analysis and defense against mass exploitation and reconnaissance, shared his expertise on network fingerprinting, a technique to identifiy and analyze the unique behaviors of devices, systems, and networks based on their network interactions. He explored the evolution of network fingerprinting, from early tools like p0f to more advanced methods such as JA4, JA4+, and MuonFP.
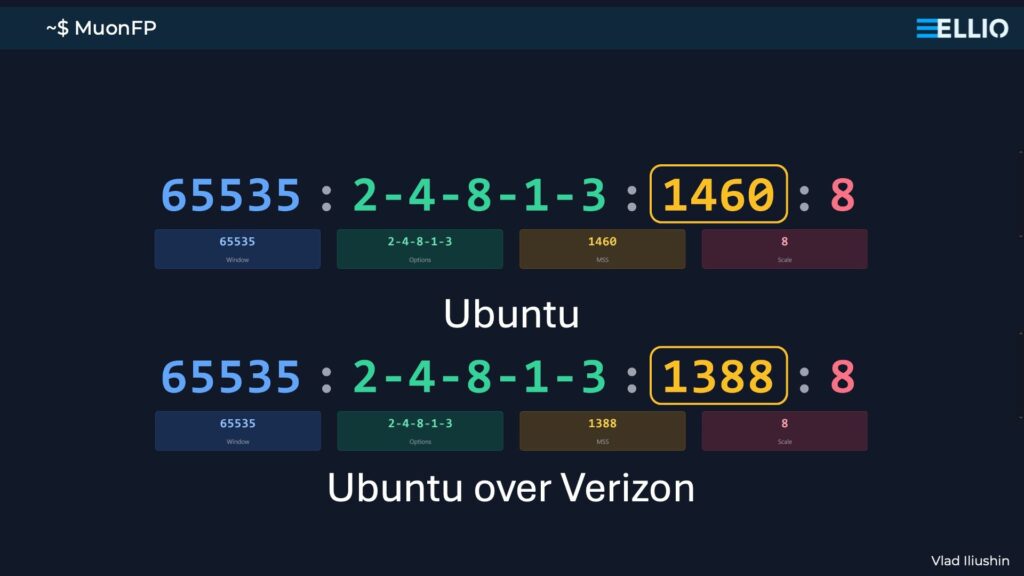
Vlad explained how modern fingerprinting techniques allow analysts to identify the tools and infrastructure used by attackers – whether they’re relying on fast scanners, basic banner grabbers, or connections masked by VPNs and jump servers. Additionally, he provided practical guidelines on how to interpret fingerprints, when to use them, and their limitations.
Collaboration matters.

Collaboration took center stage at the AMTSO Networking Reception during RSAC 2025 in San Francisco. The event brought together AMTSO members – including ELLIO – and special guests from across the industry, nonprofit sector, and government. A lively discussion on collaboration and data sharing in cybersecurity featured insights from Eva Galperin (Director of Cybersecurity, Electronic Frontier Foundation), Jon Baker (Director and Co-Founder, Center for Threat-Informed Defense at MITRE), and Sam Curry (VP & CISO in Residence, Zscaler), with moderation by Vlad Iliushin, ELLIO CEO and President of AMTSO.
At the heart of AMTSO’s mission is the belief that cybersecurity is stronger when we work together. The Real-Time Threat List (RTTL) is proof of that – a collaborative threat intelligence platform built to accelerate detection and improve malware defenses. Processing over 75,000 samples monthly, RTTL brings together contributions from AMTSO members, CERTs, and other partners to catch threats early, often before they’re seen anywhere else. With deep analysis capabilities and open access for qualified contributors, RTTL shows how shared data can lead to smarter, faster responses across the entire security ecosystem.
Footprints of the roadshow: A journey in photos.



















About ELLIO
ELLIO is a commercial research lab specializing in in-depth, real-time analysis of mass exploitation and network reconnaissance. We deliver actionable threat intelligence and advanced solutions designed to enhance cybersecurity team productivity and maximize the efficiency of existing tools. To learn more about ELLIO Threat Intelligence, Ultimate IP Blocking, and other solutions for boosting network security, security operation, and threat hunting visit ellio.tech.


