This post dives into the advantages of IP blocking and TCP fingerprinting, comparing their effectiveness and examining how combining both can maximize network security.
The inspiration for this article came from a lively conversation I had with Ken Webster, Sr. Incident Response Leader at Imperva, a Thales company. In addition to incident response and investigation, his current project involves disrupting the ‘Reconnaissance’ phase of the MITRE ATT&CK® chain to reduce exposures before adversaries can effectively target an enterprise. In support of this effort, he’s developed the open-source utilities MuonFP and Fingerprint Firewall (fpfw), which can be found on GitHub.
We will explore these technologies and their potential role in the future of enterprise security, covering various layers of the OSI model, the mathematical principles behind TCP fingerprinting, and practical strategies for implementing these crucial security measures. As cyber threats become increasingly sophisticated, relying solely on the application layer (Layer 7) is not enough. By incorporating security measures at Layers 3 and 4, organizations can better protect themselves against a wider range of attacks.
Before we dive in, it’s important to note that our discussion will focus on the advantages and disadvantages of fingerprinting and IP blocking at Layers 3 and 4, as many points may not apply to Layer 7. Additionally, we’ll be addressing ingress traffic only—focusing on protecting your network perimeter from external attacks.
You can dive directly into most important parts of this post
The Beauty of TCP/IP Layer Detections/Blocking
TCP Fingerprinting Tools: p0f, MuonFP, and JA4T
Advantages of TCP Fingerprint Blocking
Combining IP Blocking and TCP Fingerprint Blocking for Enterprises
Understanding Network Layers: L3/L4 vs. L7
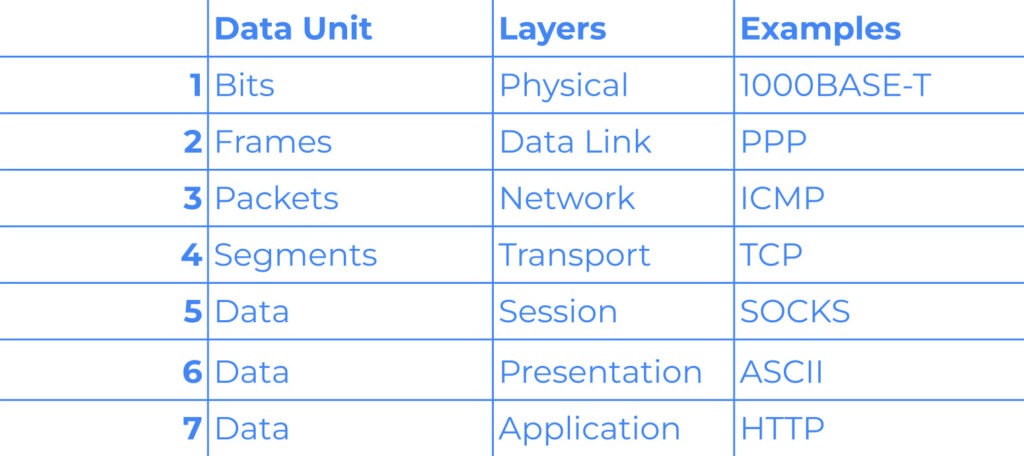
To set the stage, let’s revisit the OSI model, which divides network communication into seven layers, each responsible for specific functions. For this article, we’ll focus on three of these layers:
- Layer 3 (Network Layer): Handles IP addressing and routing. IP blocking operates here by preventing packets from known malicious IP addresses from reaching your network.
- Layer 4 (Transport Layer): Manages end-to-end communication and error checking through protocols like TCP and UDP. TCP fingerprinting operates at this layer, analyzing TCP handshake characteristics to identify malicious activity.
- Layer 7 (Application Layer): Manages high-level protocols and user interfaces, such as HTTP, FTP, and SMTP.
While many security solutions concentrate on Layer 7—such as web application firewalls (WAFs) and intrusion detection systems (IDS)—implementing security measures at Layers 3 and 4 allows for earlier detection and mitigation of threats. By addressing potential attacks before they reach the application layer, organizations can significantly enhance their defensive posture.
The Beauty of TCP/IP Layer Detections/Blocking
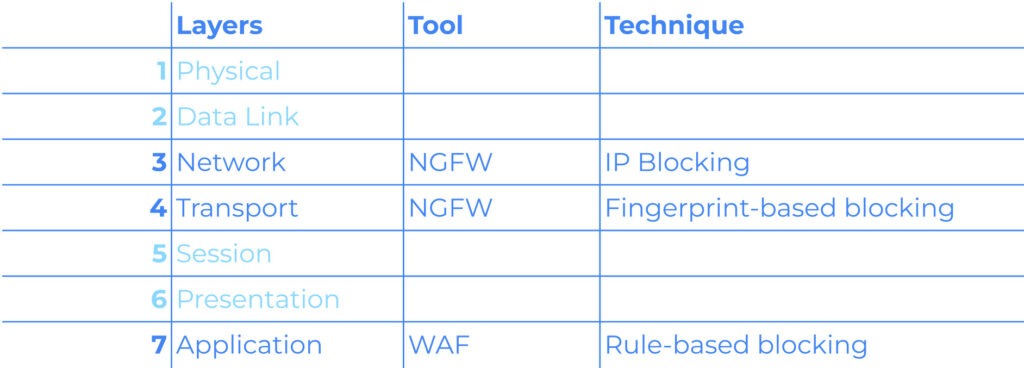
Imagine being able to stop a threat before it even knows you’re there. One of the most elegant aspects of detections at the TCP/IP layers is their resilience against many evasion techniques. If you block an IP address, it doesn’t matter how ingenious the payload is or what application the exploit targets—the malicious traffic is stopped in its tracks.
At Layer 7, detections are often more specific, targeting particular exploits or payload signatures. While effective, these can be bypassed by savvy threat actors who manipulate their payloads to evade detection. This cat-and-mouse game can leave your network vulnerable.
To appreciate the creativity attackers employ, consider exploring quines, which are programs that reproduce their own source code. This concept illustrates the ingenuity that can be applied to manipulate code and, by extension, payloads designed to bypass security measures. Understanding these tactics underscores the importance of robust defenses at lower layers, where such evasions are less effective.
TCP Fingerprinting Tools: p0f, MuonFP, and JA4T
As we dive deeper, it’s essential to understand the tools available for TCP fingerprinting and how they can bolster your network security.
The Legacy of p0f
One of the pioneers in passive operating system fingerprinting is p0f. This tool analyzes TCP/IP traffic to identify the operating system of network hosts by examining parameters like:
- TCP Window Size
- Initial Time-To-Live (TTL)
- TCP Options and their order
- Maximum Segment Size (MSS)
- Window Scaling
p0f generates TCP signatures in the following format:
sig = ver:ittl:olen:mss:wsize,scale:olayout:quirks:pclassWhile p0f has been instrumental in understanding network behavior and early attempts at fingerprinting client OSes, it is currently not as widely used. Modern host OS detection often relies on Layer 7 or a combination of L3/L4 and L7 methods. However, the principles it introduced continue to influence current tools.
Additionally, please note that in this post, we are touching only TCP fingerprinting capabilities of p0f.
MuonFP and JA4T: Making TCP Fingerprinting Easier
Building upon the foundations laid by p0f, the new generation of tools—MuonFP and JA4T (part of JA4+)—simplify TCP fingerprinting by focusing on key TCP handshake parameters:
- TCP Window Size
- TCP Options
- Maximum Segment Size (MSS)
- Window Scaling
These tools leverage the unique characteristics of TCP/IP stacks to generate fingerprints, allowing for the identification of malicious activity based on network behavior rather than just IP addresses.
If you’re interested in a deep dive into how MuonFP and JA4T work and how they can be integrated into your security strategy, let me know in the comments. Your feedback will help prioritize a future blog post dedicated to exploring these tools in detail.
Also, you can check your own fingerprints here.
MuonFP’s and JA4T’s Effectiveness Against Masscan and ZMap
To illustrate the practical impact of these tools, let’s consider how MuonFP and JA4T excels in blocking mass scanning tools like Masscan and ZMap. These tools often use default TCP configurations that result in distinctive fingerprints. For example, Masscan typically generates a fingerprint like 1024::: (MuonFP) and 1024_00_00_00 (JA4T), lacking TCP options, MSS, or window scaling—only the window size is set.
By identifying and blocking these specific fingerprints, you can effectively prevent large-scale scanning attempts. There’s even a MuonFP-based firewall available called Fingerprint Firewall (fpfw), which you can find on GitHub: sundruid/fpfw. Fpfw is designed to manage blocking of traffic based on the unique fingerprints generated by MuonFP, adding an extra layer of security to your network.
The Mathematics of TCP Fingerprinting and IP Blocking
Understanding the theoretical and practical scope of TCP fingerprints is crucial for grasping the risks and benefits of blocking based on TCP fingerprinting alone. Let’s take a journey through some numbers to appreciate the scale and possibilities.
Theoretical Combinations
IPv4 Address Space
With IPv4, the math is straightforward. There are 2³² (approximately 4.29 billion) possible IP addresses. After accounting for reserved and special-purpose addresses, about 3.7 billion IPs are available for blocking.
TCP Fingerprints
Estimating the number of possible TCP fingerprints involves several variables:
- TCP Window Size: A 16-bit field ranging from 0 to 65,535.
- TCP Options: While in theory there can be up to 256 different TCP options (based on various RFCs), in practice, only a handful are commonly used. The TCP header can include options up to 40 bytes.
- Common options include:
- EOP (0): End of Options List
- NOP (1): No Operation, used for padding
- MSS (2): Maximum Segment Size
- Window Scale (3): Scaling factor for window size
- SACK Permitted (4): Selective Acknowledgment
- Timestamps (8)
- Common options include:
- The order and combination of these options can vary, creating different fingerprints. Options are often combined using NOPs for padding, and their permutations lead to a variety of fingerprints.
- Maximum Segment Size (MSS): Typically ranges from 536 to 1460 bytes, determined by the MTU minus IP and TCP header sizes. With Jumbo frames, MSS can go much higher.
- Window Scaling: Specifies a scaling factor for the window size, with values ranging from 0 to 14, representing shift counts from 2^0 to 2^14.
Calculating the Number of MuonFP Fingerprints
- TCP Window Size Values: 65,536 possible values.
- TCP Options Combinations: Approximately 1,956 different combinations for the TCP options in the handshake.
- MSS Values: Let’s assume 1,500 potential values based on typical MTU settings.
- Window Scaling Values: 15 possible scaling factors (0 to 14).
Total Practical Combinations:
Total Fingerprints = 65,536 × 1,956 × 1,500 × 15 ≈ 288 quintillion (288,423,936,000,000,000,000).
This is a naive way of calculating TCP Fingerprint space, as many of the parameters are not independent, and I believe there is a beautiful way of calculating all possible values. Leave a comment below.
While the theoretical space of possible MuonFP/JA4T fingerprints is immense, in practice—and due to the dependent nature of some values—the space is smaller but still substantial.
Practical Observations
At ELLIO, we observe between 120,000 and 200,000 unique MuonFP/JA4T fingerprints monthly. Among these, some fingerprints stand out due to their simplicity and prevalence.
Noteworthy Fingerprints
- Simple Fingerprints:
- 1024::: (MuonFP) / 1024_00_00_00 (JA4T)
- 65535::: (MuonFP) / 65535_00_00_00 (JA4T)
- 18547::: (MuonFP) / 18547_00_00_00 (JA4T)
These fingerprints lack any TCP options, MSS, or window scaling—only the window size is set. They are characteristic of port scanners like Masscan and ZMap in their default configurations.
- Complex Fingerprints:
- 64240:2-4-8-1-3:14560:7 (MuonFP) / 64240_2-4-8-1-3_1460_7 (JA4T)
This fingerprint indicates a TCP handshake with specific options and is common among Unix-based systems or Windows Subsystem for Linux (WSL).
It’s no surprise that these fingerprints are among the most prevalent ones. If you’re performing port scanning, you need to cover the IPv4 space quickly. Tools like Masscan and ZMap perform initial port scans to identify open ports using minimal TCP configurations—without any TCP options or other settings that can slow you down.
If the attacker is sophisticated, they might use the PF_RING driver for NICs to achieve even faster scanning speeds.
Currently, our Threat List MAX contains thousands of IPs (which is a fraction of the list) that engage in such activities. We’ll explore the implications of this later in the post.
Pro Tip: If you can use wildcards in fingerprint blocking, matching *::: (MuonFP) / *:_00_00_00(JA4T) can effectively block many scanners. We will cover this in the second part of the series.
Converting p0f Signatures to MuonFP/JA4T Fingerprints
Understanding how to translate between different fingerprinting methods enhances your ability to integrate legacy data into modern tools. Let’s walk through an example conversion.
Example Conversion
Consider the p0f signature:
4:64+0:0:1460:mss*44,7:mss,sok,ts,nop,ws:df,id+:0Breaking it down:
- 4th Parameter (MSS): 1460
- 5th Parameter (Window Size): mss*44, which equals 1460 * 44 = 64,240
- 6th Parameter (Scale and TCP Options): Scale 7, options mss,sok,ts,nop,ws
Translating to MuonFP/JA4T Fingerprint:
- Window Size: 64,240
- TCP Options: 2-4-8-1-3 (where 2=MSS, 4=SACK Permitted, 8=Timestamps, 1=NOP, 3=Window Scale)
- MSS: 1460
- Window Scale: 7
Resulting in the MuonFP fingerprint:
64240:2-4-8-1-3:1460:7By running both MuonFP/JA4T and p0f side by side and making a connection, you can confirm that MuonFP indeed generates the 64240:2-4-8-1-3:1460:7 fingerprint.
By converting p0f signatures to MuonFP/JA4T fingerprints, you can integrate legacy data into modern tools, enhancing your detection capabilities without losing valuable historical insights.
Multi-Stage Scanning Scenario
To understand the strategic advantage of combining IP blocking and TCP fingerprinting, let’s examine a common multi-stage scanning scenario used by attackers.
Attackers’ Methodology
- Initial Port Scanning: Attackers use tools like Masscan to quickly identify open ports across a vast range of IP addresses.
- Secondary Scanning or Exploitation: If an interesting port is found, the information is passed to another tool or script for deeper scanning or immediate exploitation.
Benefit of Blocking Early
By blocking the initial reconnaissance with TCP fingerprinting, you hinder the attacker’s ability to proceed to the next stage. Attackers often use the same IP addresses for both scanning and exploitation, so IP blocking can prevent both stages.
For example, the IP address 185.142.236.38 (as of this writing) is listed in our Threat List MAX. This IP has thousands of TCP fingerprints associated with it, both related to scanning and application-level activity. By blocking it early, you eliminate a potential threat vector.
Spray-and-Pray Attacks
Not all attackers follow a meticulous multi-stage approach. In “spray-and-pray” scenarios, attackers skip reconnaissance and directly attempt to exploit a large number of targets without prior scanning.
- Challenge: The TCP handshake may look legitimate, as attackers use standard configurations to avoid detection—and because it’s likely an L7-level exploit.
- Solution: IP blocklisting becomes more crucial in these cases, as fingerprint-based blocking may not be effective.
Attackers may use services like Shodan and Censys to gather lists of potential targets. By including known scanner IPs in your blocklists, you can mitigate this risk and reduce exposure to such attacks.
If you let your infrastructure be searchable on the internet, congratulations—you’ve got yourself a free cloud ASM tool for your edge and perimeter. There’s just a slight downside: everyone else has access to your information as well.
Advantages of IP Blocking
Simplicity and Effectiveness
IP blocking is straightforward to implement using firewall rules or intrusion prevention systems (IPS). By blocking known malicious IPs before any connection is established, you reduce the risk of attacks and prevent unnecessary load on your servers. It is a simple, plug-and-play solution that is supported by the majority of Next-Generation Firewalls (NGFWs) and is as close to “set-and-forget” in cybersecurity as it gets.
Limitations
- Shared IP Environments: There’s a risk of false positives when legitimate users share IP addresses with malicious actors.
At ELLIO, we specialize in determining what is safe to block for our enterprise customers without disrupting their services. Our expertise lies in figuring out what to block and, most importantly, what not to block.
Advantages of TCP Fingerprint Blocking
Granularity and Precision
TCP fingerprint blocking allows you to block connections based on the specific characteristics of malicious scanners like Masscan and ZMap. It’s effective even when attackers rotate IP addresses, as their TCP stack fingerprints often remain consistent.
Limitations
- Complexity: Requires more sophisticated firewall configurations.
- Implementation Challenges: Integrating TCP fingerprint-level blocking is not as plug-and-play as deploying a dynamic IP blocklist.
Combining IP Blocking and TCP Fingerprint Blocking for Enterprises
Why Combine Both Methods?
By integrating both IP blocking and TCP fingerprint blocking, enterprises can achieve a more robust security posture.
IP blocking filters out known threats, while TCP fingerprint blocking detects specific unwanted and malicious behavior patterns, including those from unknown or rotating IPs.
Implementation Strategy
- Deploy IP Blocklists: Utilize reputable threat intelligence feeds to dynamically update firewall rules.
- Implement TCP Fingerprinting: Use tools or next-generation firewalls (NGFWs) that support TCP fingerprint analysis.
Blinding the Cyclops
By employing both methods, you effectively “blind the cyclops”—disrupting the reconnaissance activities that attackers rely on to find and exploit vulnerabilities. This metaphor underscores the power of proactive defense mechanisms in neutralizing threats before they can cause harm.
The State of Next-Generation Firewalls (NGFWs)
Lets quickly dive into the capabilities of NGFWs to effectively do IP blocking and blocking based on TCP fingerprinting.
IP Blocking Capabilities
Many vendors have implemented robust IP blocking features:
- F5: Offers IP Intelligence
- Palo Alto Networks: Provides External Dynamic Lists
- Checkpoint: Uses IOC Feeds
- Fortinet: Includes External Connectors in their Security Fabric
- OPNsense: Supports URL Tables
- SonicWall: Features Botnet Filtering
- Sophos Firewall: Third-Party Threat Feeds
- Cisco and pfSense have similar functionalities
These firewalls can fetch dynamic IP blocklists and apply them at ingress seamlessly. The hardest part is choosing the right blocklist based on your organization’s risk profile and assessment.
During the process of writing this blogpost, Sophos announced Third-Party Threat Feeds support in their v21 release, great job Sophos!
Notably, some vendors like Ubiquiti and MikroTik lag in this area, though Mikrotik offers other advanced features like running Docker containers on the firewall itself.
TCP Fingerprinting Support
With TCP fingerprinting, the landscape is less mature:
- F5: An early adopter and innovator, F5 supports JA4T in their iRules.
If you’re aware of other vendors supporting TCP fingerprinting, please let me know in the comments. The lack of widespread support highlights an area ripe for innovation and development within the NGFW market.
TCP in the Context of Reverse Proxies and CDNs
It’s important to consider how TCP fingerprinting interacts with other network technologies like reverse proxies and Content Delivery Networks (CDNs).
Impact on Fingerprinting
Reverse proxies terminate client connections and establish new ones to backend servers, obscuring the original TCP fingerprints. If someone uses traditional port scanning on the CDN or reverse proxy provider, their reconnaissance will help them identify provider infrastructure—not yours.
The TCP fingerprinting in this case is done by the provider and is used for multiple purposes, including as one of the layers in protection against DDoS attacks.
Cloudflare’s Innovative Approach
Cloudflare has been a pioneer in adopting TCP fingerprint blocking effectively. They released a p0f BPF compiler that compiles p0f signatures into bytecode for use with iptables, bridging the gap between different layers and tools. We will cover this compiler in more detail in the next part of the series.
With the modern adoption of eBPF, wouldn’t it be beneficial to have MuonFP and JA4T fingerprints for every connection, easily available in user space? This could open new avenues for advanced threat detection and mitigation.
What to Use and When
Now, let’s discuss when to use IP blocking, when to use TCP fingerprint blocking, and when to use both. While there are many technical factors to consider—like the complexity of your edge or maintenance requirements—here’s a starting point:
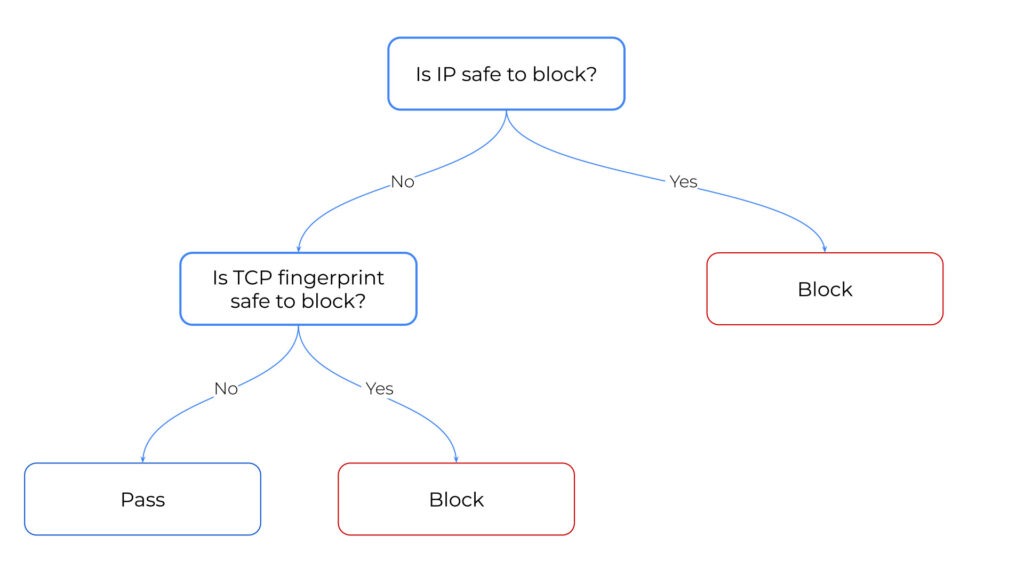
Use IP Blocking if:
- You need a simple, easy-to-deploy solution.
- You prefer minimal configuration and management overhead.
- You want to block malicious IPs effectively.
Use TCP Fingerprint Blocking if:
- You aim to prevent port scanning and reconnaissance activities.
- You have the technical capability to implement advanced firewall configurations on your edge.
Use Both IP Blocking and TCP Fingerprint Blocking if:
- You require a high-security posture against advanced and targeted threats.
- You are willing to invest in technical resources for implementation and maintenance.
- You seek a layered defense strategy to disrupt attacker reconnaissance.
Conclusion
Incorporating both IP blocking and TCP fingerprint blocking into your security strategy strengthens your organization’s defenses against a wide range of attacks. By limiting attackers’ ability to identify and target your network, you significantly reduce the risk of both broad and targeted attacks—essentially blinding the threat—the cyclops—before it can strike.
Advantages of Combining Both Blocking Methods
- IP Blocklists: Offer a straightforward, plug-and-play solution compatible with NGFWs and WAFs. They are particularly effective against spray-and-pray attacks and malicious IPs.
- TCP Fingerprint Blocking: Provides an additional layer of security by targeting the tools and methods used by attackers, even when they rotate IP addresses.
By utilizing both methods, you disrupt the attackers’ ability to see and target your network effectively, significantly reducing the risk of both broad and targeted attacks.
Acknowledgments
I would like to express my gratitude to:
- Ken Webster for his invaluable insights and for developing MuonFP and Fingerprint Firewall (fpfw).
- John Althouse and the team behind JA4+ and FoxIO, who are working on creating suits of great fingerprinting technologies.
- Michał Zalewski, creator of p0f, and all contributors to p0f whose pioneering work laid the groundwork for modern TCP fingerprinting techniques.
References
For further reading and resources, consider reviewing the following RFCs related to TCP options and extensions:
- RFC 9293: Transmission Control Protocol (TCP) Specification
- RFC 2018: TCP Selective Acknowledgment Options
- RFC 7323: TCP Extensions for High Performance
- RFC 1072: TCP Extensions for Long-Delay Paths (Obsoleted by RFC 2018, 1323, 6247)
- RFC 6247: Moving the Undeployed TCP Extensions
- RFC 1644: TCP Extensions for Transactions
- RFC 2385: Protection of BGP Sessions via the TCP MD5 Signature Option
- RFC 4782: Quick-Start for TCP and IP
- RFC 5482: TCP User Timeout Option
- RFC 5925: The TCP Authentication Option
- RFC 7413: TCP Fast Open
- RFC 4727: Experimental Values in IPv4, IPv6, ICMPv4, ICMPv6, UDP, and TCP Headers
These RFCs provide detailed information on various TCP options and extensions, which are relevant for understanding TCP fingerprinting and the TCP options used in generating fingerprints.
You can reach out to us at [email protected] to discuss fingerprint blocklists and IP blocklists.
Thank you for joining me on this exploration of IP blocking and TCP fingerprint blocking. Together, we can make our networks more secure and stay one step ahead of those who seek to exploit vulnerabilities.
Feel free to leave your comments below, and let me know if you’d be interested in a deep dive into MuonFP and JA4T in a future blog post.
Useful links
- Find out out ELLIO: Threat Intelligence to reduce alert fatigue and speed up threat hunting.
- Try ELLIO: Blocklist Management with a 7day trial.
- Use a free ELLIO IP Lookup to check suspicious IPs.
- Explore ELLIO: Threat List MAX, the largest and most dynamic IP blocklist on the market, compatible with all popular next-gen firewalls.
- Download ELLIO Free Community IP Blocklist.
More about ELLIO at https://ellio.tech



Comments 1